
The second series of "CSI:Internet" was originally published in c't magazine starting with issue 15/2011. For links to articles in the first series please refer to our CSI:Internet HQ page.
CSI:Internet
Episode 3: A trip into RAM
by Frank Boldewin
It's Friday around lunch time, and I am looking forward to taking off early for the weekend when my cell phone rings. It's my friend Wolfgang, who nervously tells me that his bank just called to say his account has been temporarily blocked. Apparently, his bank data popped up on a Russian server, and 2,000 euros have already been withdrawn from his account.
Wolfgang's bank told him that he almost certainly has a trojan on his PC, a charge he vociferously denies on the phone with me. After all, he has an updated virus scanner, a firewall, and he always keeps everything up to date. "Tell it to your bank", I say to try to discourage him from making the inevitable request for help.
"I did." Wolfgang forges ahead with his complaints, adding that it did no good – the bank just told him that it had already had numerous similar cases with other customers. And in all of them, an online banking trojan was found on their PCs. But before I can answer, the inevitable request comes. Frank, you're an expert on these things. Would you mind taking a quick look at my PC so we can prove to my bank that everything is okay on my end? After all, they're more likely to believe an expert like you.
I can't help but roll my eyes; normally, I try to get around such requests. After all, if there's one thing I have learned in ten years of virus analysis it's that there's no such thing as a "quick look". And once you get started, you find yourself practically with the job of admin for that computer. But Wolfgang is a really close friend, and I owe him one. So I let him talk me into it, and I hop on my bike.
Less than an hour later, I'm sitting in Wolfgang's office listening to the whole story once again from the beginning. While I am trying to break the news to him that it all really sounds like he has a trojan on his PC, I boot up my analysis system connected to a free port on his home router.
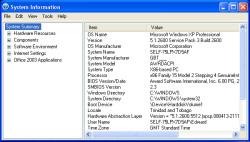
![]() The little Windows tool winmsd displays the most important system information.
The little Windows tool winmsd displays the most important system information.
Then, I take a look at Wolfgang's PC – Windows, of course. The little tool winmsd.exe shows me exactly what I am dealing with: a dinosaur with Windows XP Service Pack 3, 32-bit and 512 MB of RAM. The command ipconfig /all not only shows me the current IP address (10.64.234.28), but also that the PC got it from a system with the IP address 10.64.234.1, which apparently works as a standard gateway and DNS and DHCP server. Wolfgang proudly explains that he reconfigured the default 192.168.0 network in his WLAN router to something more sensible. My analysis system confirms that it has also received an address from this router for the network: 10.64.234.54.
Before Wolfgang tells me all he knows about reconfiguring networks, I take a closer look at his PC by inserting a USB stick with my private tool collection on it. But before I plug it in, I make sure that the little switch on the side indicates that the stick is write-protected. Unfortunately, USB sticks with such write locks have gone out of fashion and are now hard to find.
A snapshot
Since Wolfgang has already had his virus scanner conduct a complete scan to no avail, I don't waste any time with a repeat scan but instead get right to work: WinDD ftw! I simply cannot get used to the new name MoonSols Windows Memory Toolkit. Matthieu Suiche's little tool writes the current content of the physical main memory into a file and can even immediately send it to an analysis system within the network, if need be.
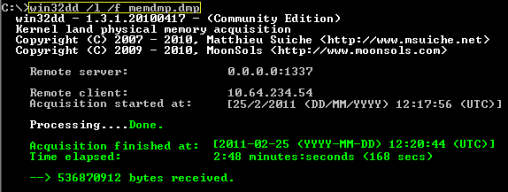
I start by selecting the patient for my analysis system by means of:
win32dd.exe /l /f memdump.dmp.
The program then waits at the elite port 1337 for an incoming connection from the client system to be investigated in order to write the incoming data into the memdump.dmp file. Because I am dealing with a 32-bit system, I also boot Wolfgang's PC with the 32-bit version of WinDD, though this time with the parameter /t 10.64.234.54, which moves the dump over to my WinDD server via the network.
Just a few minutes later, it confirms that it has received and saved 536,870,912 bytes – the complete content of the client's 512 MB of RAM. Wolfgang now seems a bit uptight, so I explain to him that I did not just copy the content of his hard drive, so he does not need to worry about his "private images." The old womaniser breathes a sigh of relief.








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








