Facebook closes cross-site scripting holes
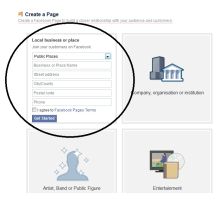
![]() Code could be injected through (fake) custom locations
Code could be injected through (fake) custom locations
Source: Break Security
Facebook has closed various cross-site scripting (XSS) holes that were discovered by security firm Break Security and which have now been described in greater detail. Break Security's CEO, Nir Goldshlager, explains that the social network was vulnerable to attacks through its Chat feature as well as its "Check in" and Messenger for Windows components.
In the Chat window, for example, attackers were able to share links that weren't adequately checked by Facebook. This enabled attackers to add disguised JavaScript commands to links that were then automatically inserted into href parameters by the Chat client. When users clicked on these specially crafted messages, the injected code was executed on their systems.
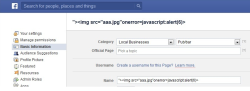
![]() Page names can contain JavaScript
Page names can contain JavaScript
Source: Break Security
The "Check in" service could be manipulated by creating custom locations into which attackers were then able to inject JavaScript code through their settings. That client-side XSS code was executed when users checked in at such a location.
Messenger for Windows could be compromised by creating a Facebook page. Pages can send messages to all users. If JavaScript code was entered as part of the page name, and the page sent out messages to users, the script would be executed on users' machines as soon as they logged into Messenger.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








