Backwards Unicode names hides malware and viruses
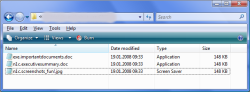
![]() Windows can handle right-to-left by default since Vista.
Windows can handle right-to-left by default since Vista.
Source: Norman
AV vendor Norman has discovered malware that camouflages its file name via special Unicode characters. For instance, they may show up as exe.importantdocument.doc in the email client or in Windows Explorer. However, an executable (EXE) file that will still be treated as such by the system, and launched when double-clicked, is hidden behind this file name.
Norman's virus analyst, Snorre Fagerland, says that this effect is caused by such Unicode characters as 0x202E (right-to-left override) and 0x202B (right-to-left embedding). When located in the right place, a file name such as cod.stnemucodtnatropmi.exe suddenly turns into some "important documents". The telltale "exe" at the beginning can be hidden further. For instance,
[RTLO]cod.yrammusevituc[LTRO]n1c[LTRO].exe
turns into the seemingly harmless n1c.executivesummary.doc when displayed in Explorer, which is unlikely to raise suspicion. However, the system will still recognise the ".exe" file extension and treat the file accordingly.
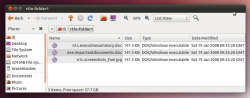
![]() Ubuntu also responds to the Unicode characters.
Windows has supported fonts that read and are displayed from right to left since Vista; under Windows XP, an extension package is required. However, the problem is by no means limited to Windows. Linux can generally also handle Unicode and was found to be vulnerable to the same spoofing trick when tested by The H's associates at heise Security. For instance, the ZIP utility and the property dialogue of an Ubuntu desktop (10.04 LTS) also displayed an apparent doc file that was, however, treated as an exe file and linked to Wine.
Ubuntu also responds to the Unicode characters.
Windows has supported fonts that read and are displayed from right to left since Vista; under Windows XP, an extension package is required. However, the problem is by no means limited to Windows. Linux can generally also handle Unicode and was found to be vulnerable to the same spoofing trick when tested by The H's associates at heise Security. For instance, the ZIP utility and the property dialogue of an Ubuntu desktop (10.04 LTS) also displayed an apparent doc file that was, however, treated as an exe file and linked to Wine.
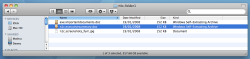
![]() In Mac OS X, Unicode is also included by default.
Mac OS X also displayed the characters according to the Unicode standard – as the supposedly harmless doc variant. However, file names and extension doesn't play as important a role on Macs and Linux as they do under Windows.
In Mac OS X, Unicode is also included by default.
Mac OS X also displayed the characters according to the Unicode standard – as the supposedly harmless doc variant. However, file names and extension doesn't play as important a role on Macs and Linux as they do under Windows.
The basic problem isn't new. In 2007, The H Security already reported on misleading file names under Vista – although this was discussed as more of a theoretical risk at the time. Norman's analyses demonstrate that the trick is now being used by malware authors, and users will therefore no longer be able to trust the file names that are being displayed. For instance, if a system repeatedly switches direction when displaying a file name, not even a palindrome expert might be able to recognise the what the real file name is.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








