Android smartphones infected via drive-by exploit - Update
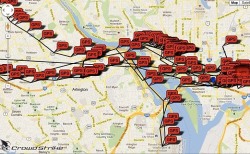
![]() Mapping the results of an Android drive-by infection
At the RSA Conference 2012, former McAfee executives George Kurtz and Dmitri Alperovitch have presented a Remote Access Tool (RAT) that infects Android smartphones (version 2.2). They used an as-yet unpatched bug in Android's WebKit browser to inject the malware. The researchers say that they bought the vulnerability information, and a range of other tools, on the black market. The finished exploit is based on 20 components that apparently cost a total of $1,400 on the black market.
Mapping the results of an Android drive-by infection
At the RSA Conference 2012, former McAfee executives George Kurtz and Dmitri Alperovitch have presented a Remote Access Tool (RAT) that infects Android smartphones (version 2.2). They used an as-yet unpatched bug in Android's WebKit browser to inject the malware. The researchers say that they bought the vulnerability information, and a range of other tools, on the black market. The finished exploit is based on 20 components that apparently cost a total of $1,400 on the black market.
The infection is based on an SMS text message allegedly sent by the user's service provider. The message contains the request to download an important update and provides a link to this alleged update. One click on the link is enough to infect the smartphone – which means that drive-by infections have now reached the smartphone world. The link downloads the malware and executes the loader; this crashes the device and installs the actual malware components while rebooting.
The demonstrated malware is based on Nickspy, a trojan that has been around for a while; the researchers bought this trojan and modified it. They also created a dedicated command and control infrastructure to control the devices. The experts estimate that the time they spent adapting and developing the necessary code was worth about $14,000.
Once installed, the trojan records phone conversations, activates the smartphone's camera, reads dialled numbers, copies stored SMS messages and transmit the phone's current location to the C&C server. The location is conveniently displayed in Google Maps, and the data can be read and transmitted by clicking on the infected phone's symbol.
Kurtz pointed out that the exploited WebKit vulnerability can, in principle, also be used to install trojans on other operating systems that run this browser. When asked explicitly about iOS, Kurtz told The H's associates at heise security that "Just like with Android, we would have to get code execution via the browser. Then we would need to escalate our privilege to root. This would allow us to bypass the app store for installation [as we did] with Android." Kurtz didn't state how much effort such an attack would involve.
At the end of their presentation, the researchers put the threat level that is created by their discovery into perspective, saying that spyware programs – even commercial spying tools – have existed for quite some time, and that drive-by infections will become part of the smartphone environment. However, "the sky is not falling, these are very targeted attacks", said Kurtz.
Update: Security expert and project team member Georg Wicherski has provided The H's associates at heise Security with further information, which paints a clearer picture. The security vulnerabilities in question have already been fixed in the Webkit trunk, but Google has not yet integrated these fixes into the Android codebase. Thus no smartphone manufacturers have yet patched their ROMs, meaning that all Android smartphones are vulnerable. Packages of ten such bugs were available from the grey market for around 1000 euros.
Wicherski performed the weaponisation of the demo exploit himself, by inserting the code which downloads and installs the backdoor. The experts estimate that this work would have a value of around $15,000. The resulting restart is not a crash, but is induced intentionally in order to activate the downloaded and installed software, added Wicherski.
The trojan installed is a standard remote administration toolkit (RAT), which the researchers found in the app store and installed as is. The only homemade software in this context was the client software for remotely controlling the smartphone.
(Uli Ries / djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








