Android holes allow secret installation of apps
 Security researchers have demonstrated two vulnerabilities that allow attackers to install apps on Android and its vendor-specific implementations without a user's permission. During normal installation, users are at least asked to confirm whether an application is to have certain access rights. Bypassing this confirmation request reportedly allows spyware or even diallers to be installed on a smartphone.
Security researchers have demonstrated two vulnerabilities that allow attackers to install apps on Android and its vendor-specific implementations without a user's permission. During normal installation, users are at least asked to confirm whether an application is to have certain access rights. Bypassing this confirmation request reportedly allows spyware or even diallers to be installed on a smartphone.
What's special about the two vulnerabilities is that they can be exploited without an attack on Android's underlying Linux kernel and function in the userspace alone. When analysing HTC devices, the security specialist known as Nils found that the integrated web browser has the right to install further packages (INSTALL_PACKAGES). Nils says that HTC integrated this functionality so that the browser can automatically update its Flash Lite plug-in. However, attackers can exploit this if they have found another browser hole.
Such browser holes in Android 2.1 were already disclosed by security firm MWR InfoSecurity (Nils happens to be its head of research) in mid-August. A browser exploit for Motorola's Droid was also released recently. To demonstrate the attack, Nils used a HTC Legend running Android 2.1. The browser hole has been closed in Android 2.2, but only about a third of users are already running this version on their devices.
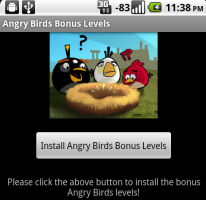
![]() This harmless looking app links to further apps resulting in charges to the user.
Android specialist Jon Oberheide demonstrated another hole which involved misusing the Account Manager to generate an authentication token for the Android Market and obtaining permission to install further apps from there. However, this initially requires a specially crafted app to be installed on the smartphone. Nothing could be easier: Oberheide released the allegedly harmless "Angry Birds Bonus Levels" app intothe Android Market and, upon installation, this app downloaded and installed three further apps ("Fake Toll Fraud", "Fake Contact Stealer" and "Fake Location Tracker") without requesting the user's permission.
This harmless looking app links to further apps resulting in charges to the user.
Android specialist Jon Oberheide demonstrated another hole which involved misusing the Account Manager to generate an authentication token for the Android Market and obtaining permission to install further apps from there. However, this initially requires a specially crafted app to be installed on the smartphone. Nothing could be easier: Oberheide released the allegedly harmless "Angry Birds Bonus Levels" app intothe Android Market and, upon installation, this app downloaded and installed three further apps ("Fake Toll Fraud", "Fake Contact Stealer" and "Fake Location Tracker") without requesting the user's permission.
The privileges of "Fake Tool Fraud" included the right to send premium SMS messages. Google has since removed all of Oberheide's apps from the Market. Back in June, Oberheide had already used an app to demonstrate an Android vulnerability. At the time, Google used the remote deletion feature, available on Android devices, for the first time.
(trk)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








