
Microsoft's struggle against bugs
By Uli Ries
It has been ten years since Bill Gates famously emailed all Microsoft's employees declaring that data protection and system security should be the company's top priorities. Uli Ries describes the subsequent progress Microsoft has achieved in making its software more secure.
The first result of Gates' email was the Trustworthy Computing Initiative, a place where Microsoft has since bundled its diverse security initiatives. Of course, Gates didn't entirely volunteer to make these topics the company's top priorities: Windows users around the world had been struggling with increasingly severe worm and virus infections for years. Nimda, Code Red and "I Love You" infected millions of Windows systems, causing businesses considerable financial losses.
![]() This email from Bill Gates set the ball rolling
This email from Bill Gates set the ball rolling
Microsoft's major corporate customers particularly went to the barricades, demanding more stable software and threatening to switch to alternative applications and operating systems. A former Microsoft executive who joined Gates in discussions with customers remembers that the CIOs of large corporations were literally shouting at the Microsoft founder. Steve Lipner also remembers these turbulent times: "When Bill's email was circulated outside of Microsoft we were ridiculed. We were facing immense security problems, and malicious gossip had it that we were trying to counteract them with emails and press releases."

Steve Lipner is like the father of SDL
Hardly anyone knows better than Lipner that Microsoft was doing more than send out memos. In 2002, it was he who announced to Microsoft's more than 8,000 Windows developers that their work had been temporarily put on hold. "We needed to educate the programmers in how to write software that is as bug-free, and therefore as difficult to attack, as possible. We developed the required training concept in only two months, and its practical implementation was indeed a bit bumpy at the beginning", Lipner remembers with a smile. Suddenly, a product's security was more important than its range of features and look – a reality that has only slowly gained acceptance in the IT world.
Developing security
Probably Lipner's most important Trustworthy Computing contribution is the Security Development Lifecycle (SDL), a strategy that is designed to enable developers to create virtually bug-free, and therefore secure, operating systems and applications. Now, more than 300 Microsoft products per year complete the company's internal SDL process – from Windows patches that are deployed as Windows updates to Xbox games and the server operating system. To allow other software companies to benefit from this concept, in 2008, Microsoft published numerous documents, videos and webcasts that describe the SDL in detail.
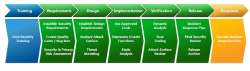
![]() The different phases of the Security Development Lifecycle
The different phases of the Security Development Lifecycle
Source: Microsoft
The SDL consists of a multitude of components that accompany a software product's development cycle. In very simplified terms, it is an extensive checklist that, depending on the product, can include more than 700 items and must be approved in full before the product is marketed. For example, the SDL stipulates the use of specific compilation settings, ASP commands and crypto technologies.
One of the SDL's accomplishments is a list of forbidden functions – the "Banned API" – which includes functions such as strcpy() that are known to be insecure. Developers must observe these bans – it isn't even possible to check code that contains functions from the Banned API into the company's version management system. This strategy allowed the SDL to eliminate in one fell swoop scores of trivial bugs that would otherwise be virtually impossible to eradicate.
The SDL also contains guidelines that regulate how and with what developers must test their source code for vulnerabilities. It challenges developers to think about potential attacks on their code (threat modelling) and requires them to systematically test their code for invalid input, for example, using fuzzing tools. Before a product is released, an "Incident Response Plan" must be created to ensure that potential future security problems are handled appropriately.
The most tangible results are the monthly security updates that have been released since October 2003. Previously, users were required to manually download updates from various areas of Microsoft's web site. Then, the company introduced the auto-update mechanism, which was later extended to include Microsoft application software and renamed Microsoft Update.
However, some experts still consider these measures insufficient. Brad Arkin, Adobe's Director of Product Security said: "If I had to make one complaint, I only wish that Microsoft decided to offer third-party software updates through Windows Update. However, allowing customers outside of enterprise environments to distribute third-party updates through Windows Update would significantly improve the update experience for all users." His request is anything but far-fetched. Linux distributions such as Ubuntu or Red Hat, for instance, update all applications via the system's update feature.
Next: Microsoft and the hackers








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








