.lnk vulnerability: Microsoft fix causes icon chaos
![]() Earlier today (Wednesday), Microsoft started offering a fix-it button on its support page that allows users to enable (or disable) a workaround which protects their systems from the effects of the unpatched vulnerability in the code for processing short-cuts (.lnk files) in all versions of Windows. Once the workaround is installed, Windows ignores program short-cut icons, which turns navigating the start menu, desktop and task bar into something of a guessing game. Previously, users who wanted to protect their systems had to manually change a registry value, which requires at least a basic level of computer skills.
Earlier today (Wednesday), Microsoft started offering a fix-it button on its support page that allows users to enable (or disable) a workaround which protects their systems from the effects of the unpatched vulnerability in the code for processing short-cuts (.lnk files) in all versions of Windows. Once the workaround is installed, Windows ignores program short-cut icons, which turns navigating the start menu, desktop and task bar into something of a guessing game. Previously, users who wanted to protect their systems had to manually change a registry value, which requires at least a basic level of computer skills.
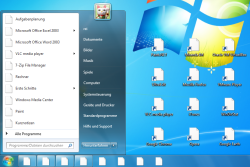
![]() Guessing game: implementing Microsoft's workaround for the .lnk flaw soon causes confusion.
Various proposed solutions to close the hole while preserving the short-cut icons have since been circulated. For instance, the LinkIconShim shell extension latches on in front of the .lnk handler to intercept potentially suspicious icon short-cuts to the control panel. However, installing the extension on one of our test systems produced an error message saying that the DLL couldn't be registered. The Ariad filter software by Didier Stevens is also said to prevent .lnk files from executing malicious code on 32-bit Windows systems. However, the author explicitly points out that this software is still in beta state, and that it's not suitable for production use.
Guessing game: implementing Microsoft's workaround for the .lnk flaw soon causes confusion.
Various proposed solutions to close the hole while preserving the short-cut icons have since been circulated. For instance, the LinkIconShim shell extension latches on in front of the .lnk handler to intercept potentially suspicious icon short-cuts to the control panel. However, installing the extension on one of our test systems produced an error message saying that the DLL couldn't be registered. The Ariad filter software by Didier Stevens is also said to prevent .lnk files from executing malicious code on 32-bit Windows systems. However, the author explicitly points out that this software is still in beta state, and that it's not suitable for production use.
As Stevens writes in his blog, in corporate environments, software restriction policies can reduce the attack surface to some degree. Such policies can ensure that program code can only be executed from specific hard disks – if the malicious code is located on a removable storage medium or on a network volume, it can be blocked. However, if a ZIP archive with infected files is unpacked on the system disk after it has been downloaded, the policies won't work.
While the Internet Storm Center (ISC) had increased the threat warning for the .lnk hole from green to yellow yesterday (Tuesday), they have now lowered it back to green level. The ISC commented that the purpose of increasing the threat level, which was to increase people's awareness of this vulnerability, has been achieved and that the level may be increased again if a major attack is observed.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








