iPhone leak is getting bigger - Update
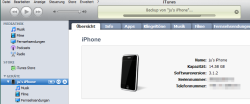
![]() Connecting an iPhone with Windows and iTunes allows a full backup of the device to be made
The iPhone's data leak is even more extensive than initially assumed. In initial tests, encrypted and locked devices essentially only disclosed music and images. However, The H's associates at heise Security have now managed to connect an iPhone with iTunes under Windows and created a full backup, including such sensitive data as passwords in clear text.
Connecting an iPhone with Windows and iTunes allows a full backup of the device to be made
The iPhone's data leak is even more extensive than initially assumed. In initial tests, encrypted and locked devices essentially only disclosed music and images. However, The H's associates at heise Security have now managed to connect an iPhone with iTunes under Windows and created a full backup, including such sensitive data as passwords in clear text.
The problem was initially discovered by Bernd Marienfeldt on an Ubuntu system. In that case the Ubuntu system displayed the various folders of a freshly booted iPhone although the phone was locked and had never had any contact with this Linux system before. A locked iPhone is supposed to refuse any communication with devices it doesn't know. However, if the iPhone is accessed while booting, this can frequently result in the phone pairing with unknown devices regardless of those protections. It appears that some system component hasn't finished booting when the connection request is made and, as a consequence, the iPhone's "lockdownd" daemon allows device pairing:
17:21:46 lockdown.c:818 lockdownd_do_pair(): ValidatePair success
The problem, though, is not with Linux or Windows, but with the iPhone. Using the same technique, heise Security also managed to pair a Windows Vista system with an iPhone. While with Linux only a few selected folders on the iPhone were displayed, Windows allowed full system access. For instance, it was no problem to create a complete backup using iTunes, including items such as notes, text messages and even plain text passwords.
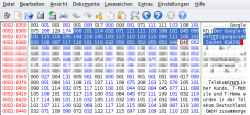
![]() Some text messages shouldn't be accessible by third parties
Some text messages shouldn't be accessible by third parties
Pairing wasn't possible with all devices. What exactly it is that determines whether the iPhone accepts a connection request remains unclear. It certainly isn't determined by the device type, because heise Security managed to trick 3G systems as well as 3GS systems. At least in one case, unwanted pairing became impossible after the iPhone's information about already paired devices was deleted. Apple has not yet answered heise Security's questions about whether and when this problem will be solved.
Update: Hector Martin and a couple of developers of the Linux packages usbmuxd and libimobiledevice have done some further research on this issue. Martin has come to the conclusion that the problem only occurs if the iPhone was shut down from an unlocked state. During the wake up this state is restored and the device is "open" for a short period of time before the Springboard application wakes up and locks it down. This short period is sufficient for a pairing to occur that ensures permanent access. An iPhone that was shut down in a locked state does not accept the pairing – which corresponds to heise Security's observations. This reduces the risk somewhat, because a lost iPhone in a locked state cannot be tricked into pairing.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








