WebGL as a security problem
 Researchers from Context Information Security are warning that the WebGL standard undermines the security concept practised by current operating system versions and offers up new attack surfaces. To enable rendering of demanding 3D animations, WebGL allows web sites to execute shader code directly on a system's graphics card. This can be exploited to take a system out completely â by, for example, getting the GPU to render especially complex 3D models or run very processor-intensive shader programs. Indeed, the Khronos Group, which is responsible for WebGL, warns of this problem in the WebGL specification.
Researchers from Context Information Security are warning that the WebGL standard undermines the security concept practised by current operating system versions and offers up new attack surfaces. To enable rendering of demanding 3D animations, WebGL allows web sites to execute shader code directly on a system's graphics card. This can be exploited to take a system out completely â by, for example, getting the GPU to render especially complex 3D models or run very processor-intensive shader programs. Indeed, the Khronos Group, which is responsible for WebGL, warns of this problem in the WebGL specification.
The researchers report that they have been able to elicit a blue screen of death (BSOD) by using targeted overloading of the graphics cards. According to the report, this could allow an attacker to exploit any security vulnerabilities in the graphics card driver to, for example, inject malicious code onto the system. Although Windows 7 and Vista have a mechanism for resetting an overloaded graphics card after about two seconds, the researchers found that this too results in a blue screen of death after a certain number of resets.
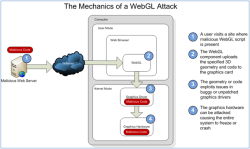
![]() If a graphics card driver contains vulnerabilities, WebGL could allow injection of malicious code onto a system.
If a graphics card driver contains vulnerabilities, WebGL could allow injection of malicious code onto a system.
Source: Context IS
The researchers were also able to use WebGL to get around the same-origin policy. WebGL uses HTML5's canvas element to draw objects in the browser. The canvas element has an 'origin-clean' flag; as long as this flag is set, the web site from which the WebGL script originates can read the content of the canvas (getDataURL). As soon as the user draws content â such as images and clip art â from other domains in the canvas or loads content from other domains as a texture, this flag is reset. This is intended to prevent web sites from being able to read and view the canvas when it contains content from other web sites.
Using some clever shaders programmed in WebGL, it is, however, possible to determine the structure of an embedded texture using run time tests and thus to reconstruct the content of a downloaded image without accessing the image directly. The researchers have released an online demo to illustrate the problem and a video of an attack can be found here (direct .avi link).
In the researchers' opinion, WebGL is simply not yet ready for primetime. They advise users and IT administrators to think seriously about deactivating WebGL support in their browsers. The latest versions of Firefox, Chrome and Safari all support WebGL. Opera has released an Opera 11 preview with WebGL support.
Update: The Khronos Group have now responded to the claims in Context's report.
See also:
- GDC: 3D in your browser â WebGL 1.0 is finished, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








