Video conferencing systems as spying tools

![]() The zoom feature allowed the security expert to read passwords that were written on documents
The zoom feature allowed the security expert to read passwords that were written on documents
Source: Rapid7
During an investigation conducted over the course of three months, security expert HD Moore found that many video conferencing systems can be easily accessed over the internet. Moore scanned around 3% of accessible IP addresses and identified 250,000 systems that support the H.323 protocol used by video conferencing systems. Moore said that almost 5,000 of them were configured to automatically answer incoming video calls – particularly devices manufactured by Polycom, a company that reportedly continues to ship most of its models with the auto-answer feature enabled by default.
The security expert said that this allowed him to monitor numerous corporate boardrooms, inmate-lawyer consultation areas, venture capital firms and research facilities; making them an easy target for industrial spies. Moore noted that the systems offered remarkable audio and video quality – in many cases, he said that he was able to remotely control the camera, for example to zoom into a note that was six metres away to read the password written on it. The expert added that he was also able to determine passwords entered by users by filming the keyboard (shoulder surfing).
According to Moore, administrators typically allocate public IP addresses to video conferencing systems because firewalls often struggle with the H.323 protocol, and many systems are insufficiently prepared for this situation, offering little or no protection for their web interfaces, telnet connections and other services.
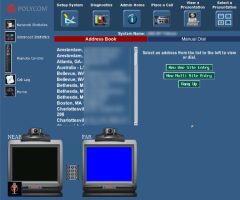
![]() HD Moore found address books on the web interfaces listing further companies that he could also access without authorisation
HD Moore found address books on the web interfaces listing further companies that he could also access without authorisation
Source: Rapid7
He explained that the web interfaces of insufficiently protected conferencing systems even enabled him to work his way through to otherwise adequately protected third-party systems: according to the report, corporate conferencing systems are often configured to automatically receive calls from specific parties. Moore said that he used an insufficiently protected system to call other parties that trusted the system he was calling from. He found the necessary IP addresses in the address book included as part of the web interface.
Moore estimates that the situation is even more drastic for systems that are accessible via ISDN: "My gut feel is that for every exposed device found on the public internet, there are twenty more attached to an obscure ISDN number that the IT department may have forgotten about." Administrators can detect H.323 systems on their networks with tools such as the h323_version module for Metasploit.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








