Trojan spreads via new Windows hole
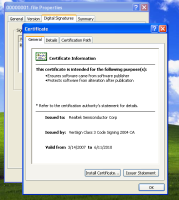
![]() The trojan carries a valid, digital signature from "Realtek".
Anti-virus specialists report that a new trojan is spreading via USB flash drives, apparently exploiting a previously unknown hole in Windows. According to analyses by Belarusian AV vendor VirusBlokAda, a copy of the trojan managed to infect a fully patched Windows 7 system (32-bit) without having to resort to such common auto-start tools as autorun.inf when a Flash drive carrying the trojan was plugged in. Instead of spreading through auto-start, the malware exploits a flaw in the code for processing short-cuts (.lnk files): Once the relevant icon is displayed in Windows Explorer, malicious code is launched without any further user interaction.
The trojan carries a valid, digital signature from "Realtek".
Anti-virus specialists report that a new trojan is spreading via USB flash drives, apparently exploiting a previously unknown hole in Windows. According to analyses by Belarusian AV vendor VirusBlokAda, a copy of the trojan managed to infect a fully patched Windows 7 system (32-bit) without having to resort to such common auto-start tools as autorun.inf when a Flash drive carrying the trojan was plugged in. Instead of spreading through auto-start, the malware exploits a flaw in the code for processing short-cuts (.lnk files): Once the relevant icon is displayed in Windows Explorer, malicious code is launched without any further user interaction.
The trojan exploits this to install two drivers with rootkit functions designed to hide its subsequent activities within the system. Interestingly, both drivers are signed with a code-signing key by vendor RealTek and can, therefore, be installed on a system without triggering an alert. Only recently, AV vendor F-Secure pointed out that the amount of signed malware for Windows is increasing. In some cases, digital keys have even been stolen from developers.
An investigation by malware analyst Frank Boldewin has shown that this is not just any old trojan designed to harvest passwords from unsuspecting users. It appears that the malware specifically targets process control systems and their visualisation components. The trojan is, therefore, unlikely to spread on a large scale.
During his investigation, Boldewin came across some database queries the trojan made that point towards the WinCC SCADA system by Siemens. As Boldewin explained in an email to The H's associates at heise Security, a "normal" malware programmer wouldn't have managed to do that. Boldewin continued "As this Siemens SCADA system is used by many industrial enterprises worldwide, we must assume that the attackers' intention was industrial espionage or even espionage in the government area". Frank Boldewin is the author of the feature article "Episode 2: The image of death" in our "CSI:Internet" series.
Microsoft has been informed about the vulnerability, but appears to have problems with reproducing it. Andreas Marx of AV-Test says that every .lnk file is linked to the ID of the newly infected USB Flash drive. This means that the sample trojans found so far can't simply be started on an arbitrary Windows system – the malware will only start in the OllyDbg debugger after some modifications to the code.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








