Test for compromised email accounts
![]() Serversniff can be used to see if a users email account has been compromised.
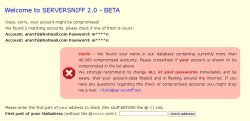
Users who fear that the access credentials of their email accounts have appeared on the recently published list can now run a test to check. On Serversniff, Thomas Springer has set up a page that checks whether an email address appears on the known lists. To run the test, users simply enter the part of their email address before the "@" and the system will display any matching entries. However, only the first and last letter of the password will appear.
Serversniff can be used to see if a users email account has been compromised.
Users who fear that the access credentials of their email accounts have appeared on the recently published list can now run a test to check. On Serversniff, Thomas Springer has set up a page that checks whether an email address appears on the known lists. To run the test, users simply enter the part of their email address before the "@" and the system will display any matching entries. However, only the first and last letter of the password will appear.

![]() Buy over 10,000 account credentials, receive a 10 per cent discount.
One may feel inclined to ask why the email providers, who also have access to these lists, haven't offered a similar service. Email providers such as Microsoft, Yahoo and Google initially assured users that all those affected had been informed and the compromised accounts had been blocked. However, it turned out that the list still contained valid access credentials for accounts used, for instance, to initiate password resets with services like PayPal, even days after the incident became known.
Buy over 10,000 account credentials, receive a 10 per cent discount.
One may feel inclined to ask why the email providers, who also have access to these lists, haven't offered a similar service. Email providers such as Microsoft, Yahoo and Google initially assured users that all those affected had been informed and the compromised accounts had been blocked. However, it turned out that the list still contained valid access credentials for accounts used, for instance, to initiate password resets with services like PayPal, even days after the incident became known.
Meanwhile, Rik Ferguson of Trend Micro has put the incident into perspective, explaining that 10,000 stolen email accounts are nothing out of the ordinary. According to Ferguson, they cost about $90 in the free market – after applying the usual 10 per cent discount. The only unusual aspect of this incident is that the data was published on the internet, he said.
See also:
- Some phished Yahoo and Hotmail accounts still open, a report from The H.
- Up to 20,000+ Windows Live Hotmail account details leaked online, a report from The H.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








