P2P botnets much larger than they seemed
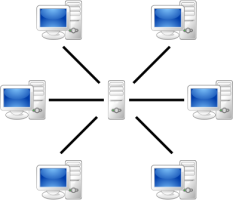
![]() A conventional, centralised network can be shut down by eliminating the central node
A conventional, centralised network can be shut down by eliminating the central node
The large-scale botnets ZeroAccess and Sality apparently control more than one million infected computers using peer-to-peer communication; the well-known online banking trojan Zeus has just about reached 200,000 nodes. An international team of researchers sneaked "sensors" into the networks to determine these figures. The P2P botnets also turned out to be much more resistant than originally thought to attempts to shut them down with targeted operations.
Conventional botnets receive their orders from a central command-and-control server, which also constitutes their main weak point. If that server is shut down, the botnet master loses control of the infected computers. For some time now, newer botnets have been using decentralised peer-to-peer structures like the ones used in file-sharing networks. In this situation, the infected systems network with each other, and each zombie computer has a list of direct communication partners – its peers – which belong to the same botnet.
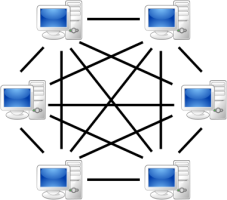
![]() When you're dealing with a peer-to-peer network, shutting down one single server is no longer enough
When you're dealing with a peer-to-peer network, shutting down one single server is no longer enough
So far, the strategy for figuring out the size of a P2P botnet has been to query peer lists from known bots and then go from one to the next in the hope that, eventually, all of the infected systems will be tracked. Such "crawling", however, results in figures that are far too low, according to Christian Rossow, Dennis Andriesse, Tillmann Werner, Brett Stone-Gross, Daniel Plohmann, Christian J. Dietrich and Herbert Bos, who sneaked their own systems into the P2P botnets; those systems actively participated in communication and were thus able to register all the active bots. In just one day, their sensors detected more than 920,000 computers under the control of one instance of Sality. The crawlers had found only 22,000 of the botnet's victims.
One major reason for the significant differences is that botnet clients are quite picky these days about which computers they add to their active peer list. Home computers, for example, are almost never included, since it is difficult to get past a NAT router from the outside.
There's more bad news when it comes to shutting these botnets down. One approach that is frequently discussed is sinkholing, in which security specialists try to fill the bots' peer lists with their own systems' addresses in order to put a stop to communication within the P2P network. In their investigation, however, the researchers realised that some of the P2P botnets are more resistant to that strategy than originally thought. Sality, for example, has an internal reputation system for communication partners, and it is difficult to take the place of a real bot with a high rating in the peer list.
The researchers' findings are based largely on analyses of actual bots; in their paper "P2PWNED: Modeling and Evaluating the Resilience of Peer-to-Peer Botnets"![]() , they also present a method for describing P2P botnets with formal models that can then also be used to simulate certain operations.
, they also present a method for describing P2P botnets with formal models that can then also be used to simulate certain operations.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








