Kobil smartcard reader hacked

![]() No broken seals: A Windows tool allows unsigned firmware to be installed.
A vulnerability in smartcard readers made by vendor Kobil allows intruders to install specially crafted firmware without opening the sealed housing. Attackers could exploit this to read PINs such as those used for digital document signatures or to display forged data on-screen. To prevent such intrusions from happening, smartcard readers are usually subjected to a special security check before they are approved. Several leading institutions had tested the Kobil readers and confirmed that they complied with the strict German Signature Law (SigG) including the German Federal Office for Information Security (BSI). The German Central Credit Committee (Zentraler Kreditausschuss, ZKA) also approved the TriB@nk device for use with the "Geldkarte" application, and Secoder, the successor of HBCI, for home banking.
No broken seals: A Windows tool allows unsigned firmware to be installed.
A vulnerability in smartcard readers made by vendor Kobil allows intruders to install specially crafted firmware without opening the sealed housing. Attackers could exploit this to read PINs such as those used for digital document signatures or to display forged data on-screen. To prevent such intrusions from happening, smartcard readers are usually subjected to a special security check before they are approved. Several leading institutions had tested the Kobil readers and confirmed that they complied with the strict German Signature Law (SigG) including the German Federal Office for Information Security (BSI). The German Central Credit Committee (Zentraler Kreditausschuss, ZKA) also approved the TriB@nk device for use with the "Geldkarte" application, and Secoder, the successor of HBCI, for home banking.
In its report on the affected Kobil devices, EMV-TriCAP Reader, SecOVID Reader III and KAAN TriB@nk, the BSI found![]() (German language link): "A firmware signature verification which uses the asymmetric ECDSA algorithm and a bit length of 192 guarantees firmware integrity and authenticity when loading new firmware into the chip card reader." This means it should be impossible to install firmware that does not have a vendor signature.
(German language link): "A firmware signature verification which uses the asymmetric ECDSA algorithm and a bit length of 192 guarantees firmware integrity and authenticity when loading new firmware into the chip card reader." This means it should be impossible to install firmware that does not have a vendor signature.
The reader's boot loader is responsible for checking the signature. A hacker using the name Colibri has managed to bypass the signature check by replacing the reader's boot loader with a specially crafted boot loader. The hacker introduced individual flash memory blocks in the wrong order, so that the memory contained some parts of the crafted boot loader and some parts of Kobil's signed boot loader – which was eventually accepted by the device. However, the crafted boot loader's signature check function was disabled, which allowed the hacker to flash arbitrary firmware onto the reader via USB. Colibri informed Kobil about the problem and released a fascinating and detailed report (German language link) about the hack, as well as a Windows tool and firmware updates for reproducing the issue. Using this information, The H's associates at heise Security successfully managed to inject specially crafted firmware into a "Kaan Trib@nk" smartcard reader (version 79.22).
At the end of April, Kobil released security update 79.23 for the Kaan TriB@nk to close the hole(s). According to Kobil's Head of Product Management and Development, Markus Tak, the update is also designed to prevent attackers from randomly updating memory blocks in the future.
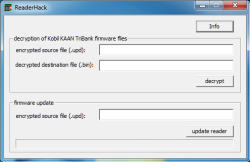
![]() The firmware can be replaced in just a few steps using a Windows tool.
Although the hole was disclosed several weeks ago, publicly available information about this problem still remains sparse. While the German Federal Network Agency, being the responsible authority under section 3 of the German Signature Law (SigG), has issued a warning (German language link) about the security hole on its web pages, the information so far doesn't seem to have reached the general user base.
The firmware can be replaced in just a few steps using a Windows tool.
Although the hole was disclosed several weeks ago, publicly available information about this problem still remains sparse. While the German Federal Network Agency, being the responsible authority under section 3 of the German Signature Law (SigG), has issued a warning (German language link) about the security hole on its web pages, the information so far doesn't seem to have reached the general user base.
When asked, the ZKA said that the vulnerability was not publicised because the issue affected a "limited group of customers" who were apparently informed directly by the vendor. Furthermore, the ZKA said that the applications for Geldkarte, HBCI and Secoder are not affected by the hole. However, the ZKA's press spokesperson was unable to explain why this should be the case.
Some savings banks have at least pointed out the problem on their web pages and recommend (German language link) that users send their devices to Kobil, for an update. Potential residual risks reportedly make it advisable that users don't update the firmware themselves. In any case, the new firmware hasn't yet been certified. Kobil has not provided any updates for its EMV-TriCAP Reader and SecOVID Reader products, which are also affected.
Talking to heise Security, Colibri gave his hack an intermediate difficulty rating. The hacker said he has analysed devices as a hobby for years and considers other projects such as his analysis of the PowerVU encryption used in military transmissions much more difficult. Colibri said the most involved aspect of the hack was having to write a disassembler for the Toshiba processor used in Kobil's devices.
The vulnerabiltiy casts further bad light on security certifications for systems and software. Prof. Dr. Rainer W. Gerling, the Data Protection and IT Security Officer at the Max Planck Society for the Advancement of Science said in an interview with heise Security: "This hack shows that the quality of a certification depends on the creativity and imagination of the tester. This is a fundamental problem of certifications." It seems that the BSI testers were not the only ones who lacked imagination, because T-Systems also found![]() (German language link) in an independent test that the devices comply with the safe PIN entry requirements described in the German Signature Law and Signature Regulation.
(German language link) in an independent test that the devices comply with the safe PIN entry requirements described in the German Signature Law and Signature Regulation.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








