Is the Conficker worm showing its hand?
People have been speculating, waiting and prognosticating, but until now the extremely cleverly programmed Conficker worm has limited itself to mainly defensive measures, such as opening various communications channels (Conficker.C can set up peer-to-peer networks with other infected systems) in order to transform itself with downloaded code, and to actively combating anti-virus software and security analysis tools. Even on 1 April, the known date on which Conficker.C would be looking for updates, virtually nothing happened. Now however, money is involved: computers infected with the Conficker worm are downloading the scareware program "SpywareProtect2009".
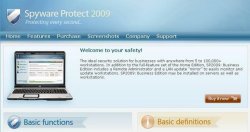
![]() Is this what Conficker is spreading?
Is this what Conficker is spreading?
Swindlers are earning a lot of money with scareware products like "Antivirus 2009", "Malwarecore", "WinDefender", "WinSpywareProtect", "XPDefender" and yes, "SpywareProtect2009". These scareware scams run a small injected program that alarms users by constantly displaying pop-up messages warning that their PCs are infected. Non-expert users can be persuaded to pay money for these bogus anti-virus products, typically bearing familiar-sounding names. In the best case, they've lost their money but nothing more. Worst case, the software they've bought actually loads malware on to the PC that may well transform it into a bot, a conduit for spam. Over a brief period late last year, for example, Microsoft removed scareware from almost a million Windows PCs with its Malicious Software Removal Tool (MSRT). More information is given in the The H article Thieves and Charlatans - Rogue Anti-virus Products.
An analysis by Kaspersky Labs says the infected zombies use their peer-to-peer structures to exchange the Conficker update as well as the address of servers in the Ukraine from which they then download and install "SpywareProtect2009". This then of course "discovers" a variety of threats, and asks users to pay $49.95 (Visa or Mastercard accepted) to get them removed. The Ukraine has already played a role: Conficker.A contained a suicide switch that was triggered whenever the worm discovered that a Ukrainian keyboard was in use.
Felix Leder and Tillmann Werner, both of Bonn University, recently made news by demystifying the Conficker worm, and Leder now reports that the new Conficker variant is blocking further domains, among them the Bonn University server with the Conficker test. This has therefore been provisionally relocated.
See also:
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








