Hardware keyloggers found in public libraries
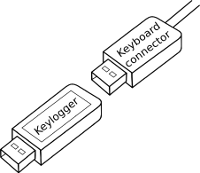 Cheshire police are investigating after hardware keyloggers had been found fitted to computers in public libraries. According to the BBC, two devices were found by library staff on computers at Wilmslow library and one on a computer at Hanforth library. At this point it is not known how long the devices have been connected. Security at the libraries has now been stepped up, with computers being checked more frequently and keyboard leads being plugged in to more visible ports at the front of the machines.
Cheshire police are investigating after hardware keyloggers had been found fitted to computers in public libraries. According to the BBC, two devices were found by library staff on computers at Wilmslow library and one on a computer at Hanforth library. At this point it is not known how long the devices have been connected. Security at the libraries has now been stepped up, with computers being checked more frequently and keyboard leads being plugged in to more visible ports at the front of the machines.
As the Manchester Evening News reported, the concern is that some members of the public use these library computers for online financial transactions and their banking details may have been the target for these attacks.
Hardware keyloggers are not illegal and can be purchased from suppliers such as Amazon for around £40. In use they are connected in-line with the keyboard and store keystrokes into non-volatile memory. Capacities of several Gigabytes are claimed to allow storage of several years of keyboard input. No software need be installed on the host computer and the keylogger memory contents can be retrieved by entering a password or key combination on the keyboard. Typically, hardware keyloggers do not support remote data retrieval, so criminals installing the loggers on public machines would have to occasionally visit the machine to retrieve any gathered data. The advantages of using a hardware keylogger are that they work regardless of the operating system the host machine is running, require little expertise to use and they are very hard for anti-malware software to detect.
Legal uses of hardware keyloggers include writers using them for a safety backup of their work, businesses monitoring employees' computer use and parents monitoring their children. Criminals using these devices break the law because they steal the gathered data and then attempt to use it to commit fraud.
(trk)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








