Botnet hidden in the Tor network

![]() Communication between a normal botnet and a C&C server
Communication between a normal botnet and a C&C server
Source: GData
The Security Street blog has found a botnet client, the operator of which is hiding behind the Tor network. This trick makes the work of security experts and criminal prosecutors much more difficult. The malicious botnet software, called "Skynet", is a trojan that Security Street found on Usenet. At 15MB, the malware is relatively large and, besides junk files intended to cover up the actual purpose of the download file, includes four different components: a conventional Zeus bot, the Tor client for Windows, the CGMiner bitcoin tool and a copy of OpenCL.dll, which CGMiner needs to crack CPU and GPU hashes.
Claudio Giarnieri and Mark Schloesser write that they recently stumbled on the unusual botnet and, at first, had problems figuring out its origin. Although they did notice parallels between Skynet and information posted by GData in September about a similar Tor botnet. An analysis of the client showed that it uses Tor hidden services, which were added to the Tor network to allow the use of internet services without letting their server IP addresses be tracked. This feature of the Tor network can protect whistleblowers, but it can also provide a sanctuary to botnet operators.
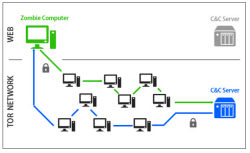
![]() If the C&C server is hidden in the Tor network, it can be difficult to identify its operator
If the C&C server is hidden in the Tor network, it can be difficult to identify its operator
Source: GData
Security experts and criminal prosecutors therefore have some obstacles to face before they can locate and shut down the C&C server. To determine which IP addresses a conventional botnet is talking to, it is usually sufficient to analyse its client's communications. The investigators can then shut down those addresses or take them over in order to put a stop to the entire botnet. With Tor hidden services, however, the zombies don't talk directly to their C&C server; instead, they use the Tor network to contact a service with a pseudo-address like x3wyzqg6cfbqrwht.onion, which resolves to the server on the Tor network. Multiple Tor nodes are interconnected as communication points at all times, which means that there is never a direct connection between the client and the server. Nevertheless, the operator can still use the typical IRC protocol for communication and does not need to implement a new protocol.
However, like Tor in general, its hidden services are neither particularly fast nor reliable, which are big problems when reliable real-time communication with thousands of clients is required. That may be why, despite being frequently discussed for years, concrete implementations of the concept have rarely been seen out in the wild.
Update: Details about the authors of the blog post have been clarified.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








