Anti-virus vendors offer free LNK protection - Update
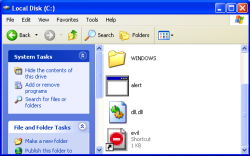
![]() The G Data tool replaces the icons of suspicious LNK files.
As malware exploiting the unpatched vulnerability in the code for processing short-cuts (.lnk files) in all versions of Windows, is spreading fast, it's high time that users obtain protection. Two AV vendors, G Data and Sophos, have come forward to fill the gap left by the absence of a patch from Microsoft.
The G Data tool replaces the icons of suspicious LNK files.
As malware exploiting the unpatched vulnerability in the code for processing short-cuts (.lnk files) in all versions of Windows, is spreading fast, it's high time that users obtain protection. Two AV vendors, G Data and Sophos, have come forward to fill the gap left by the absence of a patch from Microsoft.
As a protective measure, Microsoft has recommended that users apply a Fix-it which disables the display of all short-cut icons. However, this can cause considerable confusion on the desktop and has prompted the AV vendors to provide tools that are more discerning. The tools install a dedicated icon handler for LNK files which only blocks the display of suspicious short-cuts.
G Data's LNK-Checker worked reliably in short tests by The H's German associates at heise Security. The icons of all demo exploits tested were displayed as "no entry" signs, while normal short-cuts continued to function as before. However, users can still click on malicious LNK files and start the malware manually, unless it's blocked by a virus checker.
![]() Update - As it turns out, the G Data LNK-Checker detects all links associated with the Windows Control Panel as dangerous. This is easily demonstrated, either by dragging the Control Panel icon from the Start menu onto the desktop, or by opening the Control Panel window and dragging any of the icons it contains onto the desktop. G Data then falsely marks the new short-cut with the ban icon.
Update - As it turns out, the G Data LNK-Checker detects all links associated with the Windows Control Panel as dangerous. This is easily demonstrated, either by dragging the Control Panel icon from the Start menu onto the desktop, or by opening the Control Panel window and dragging any of the icons it contains onto the desktop. G Data then falsely marks the new short-cut with the ban icon.
The Short-cut Exploit Protection Tool by Sophos also attempts to intercept malicious LNK files and instead of the icon, presents a warning dialogue :
Potential exploit found in shortcut [name.lnk].
Prevented launching file [name.lnk]
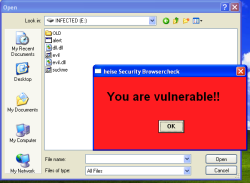
![]() The Sophos tool doesn't offer full protection. In our example, a LNK file on a USB Flash drive starts a program.
However, the protection offered by this tool is limited. For instance, the relevant software documentation states that the tool does not respond to files stored on local hard disks. Therefore, users can still infect their systems, for instance, by unpacking a ZIP archive. In the short test carried out by heise Security, a demo LNK exploit on a USB Flash drive also managed to start further programs on the local hard disk, which presents another unnecessary risk. When asked by heise Security, Graham Cluley at Sophos confirmed that this behaviour is a conceptual issue.
The Sophos tool doesn't offer full protection. In our example, a LNK file on a USB Flash drive starts a program.
However, the protection offered by this tool is limited. For instance, the relevant software documentation states that the tool does not respond to files stored on local hard disks. Therefore, users can still infect their systems, for instance, by unpacking a ZIP archive. In the short test carried out by heise Security, a demo LNK exploit on a USB Flash drive also managed to start further programs on the local hard disk, which presents another unnecessary risk. When asked by heise Security, Graham Cluley at Sophos confirmed that this behaviour is a conceptual issue.
Both tools function independently of the AV software installed on a system. We installed the programs without problems and removed them again by reopening the installer. heise Security concludes that, at present, the tool by G Data is clearly the preferable alternative to Microsoft's Fix-it solution.
Confirmed by the increasing number of actual infections beginning to emerge, users should take precautionary measures to protect their systems. For instance, talking to heise Security, the press spokeswoman of Daimler AG, Helen Däuwel, confirmed reports about virus problems in the car manufacturer's corporate network. Last week, the propagation of a virus called W32.Changeup apparently forced admins at Daimler to switch off several file servers. In very few cases – Däuwel spoke of less than one per cent – the virus variants included W32.Changeup.C, which targets the LNK hole as well as other vulnerabilities. The spokeswoman didn't wish to comment on how the worm got into the network, but said that the situation is now back under control.
See also:
- Microsoft confirms USB trojan hole, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








