Anti-virus software fails to deal with government trojan
 Since last Monday at the latest, all virus scanners will issue an alert when an attempt is made to load the trojan that was exposed by the Chaos Computer Club (CCC) onto a computer. However, to think that one is therefore protected from the government-procured spyware would be a serious mistake. Anti-virus software hardly stands a chance against such malware; some of the alerts have even turned out to be proper dummies.
Since last Monday at the latest, all virus scanners will issue an alert when an attempt is made to load the trojan that was exposed by the Chaos Computer Club (CCC) onto a computer. However, to think that one is therefore protected from the government-procured spyware would be a serious mistake. Anti-virus software hardly stands a chance against such malware; some of the alerts have even turned out to be proper dummies.
Even as late as Saturday morning, not a single AV program recognised the files as a threat. Now, most programs issue an alert along the lines of "backdoor.R2D2" when they encounter one of the files that were released by the CCC. This is intended as a measure to boost users' confidence.
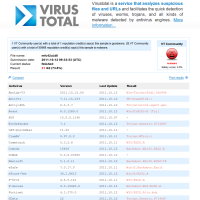
![]() Most virus scanners now issue some R2D2 alert when they encounter one of the trojan files
However, a test conducted by The H's associates at heise Security on Monday found that programs such as Ikarus, Panda, Trend Micro and McAfee stopped issuing alerts as soon as even a minimal change was made to the file. The testers simply replaced the capital O in the "DOS" string with a small o. While McAfee identified the mfc42ul.dll file as
Most virus scanners now issue some R2D2 alert when they encounter one of the trojan files
However, a test conducted by The H's associates at heise Security on Monday found that programs such as Ikarus, Panda, Trend Micro and McAfee stopped issuing alerts as soon as even a minimal change was made to the file. The testers simply replaced the capital O in the "DOS" string with a small o. While McAfee identified the mfc42ul.dll file as Artemis!930712416770 before the modification was made, it remained silent afterwards.
The fact that three of the most prominent promoters of "in-the-cloud" detection should get caught out is no coincidence, because primitive cloud detection mechanisms only use the hash values of the files in question. These values change when only a single bit is modified in a file. As the CCC had already modified![]() the files before disclosing them, the AV signatures wouldn't work with the original, unmodified files in the first place. Even if an AV vendor has added to its database the hashes of all the trojans that were submitted to the CCC – a trojan that is assigned to a different case will have a different case number, and probably also a different version number. Sometimes it takes Ikarus, Panda, Trend Micro and McAfee several days longer than the other vendors to produce proper signatures that will also detect slightly modified versions.
the files before disclosing them, the AV signatures wouldn't work with the original, unmodified files in the first place. Even if an AV vendor has added to its database the hashes of all the trojans that were submitted to the CCC – a trojan that is assigned to a different case will have a different case number, and probably also a different version number. Sometimes it takes Ikarus, Panda, Trend Micro and McAfee several days longer than the other vendors to produce proper signatures that will also detect slightly modified versions.
However, that even such local signatures can easily be bypassed is demonstrated by online banking criminals on a daily basis. And it is quite obvious that even the heuristics modules used by AV vendors to identify unknown malware aren't up to the task, because if they were, they would have issued alerts even before the CCC's disclosure. One of the likely reasons why they didn't is that the government trojan dispenses with many components that come as standard with most current run-of-the-mill trojans. For instance, the trojan doesn't attempt to hook into browsers, it doesn't read encrypted https traffic, and it doesn't act as a spam generator.
The CCC's analysis also demonstrates how the trojan manages to slip its remaining suspicious activities, such as launching a file that was downloaded from the internet, past the vendors' heuristics. It splits up the reference to the required function of the Windows API into "Crea" + "teProc" + "essA" and will only reassemble the fragments to form the suspicious "CreateProcessA" function at runtime.
Therefore, behaviour recognition remains as the frightened user's last and only hope. Many AV vendors have indeed been quick to point out that is only the static signature and heuristics detection which has failed. We are told that, should the trojan actually be launched on a system, the AV software's behaviour recognition component would immediately step in. Unfortunately, we will never find out whether this is the case, because the CCC has only tested static detection; performing the required tests now wouldn't make sense, as it is impossible to disable just the signature detection component, which will now respond to the threat.
However, doubts about whether a behaviour recognition module would really provide preventive protection are quite justified. The behavioural patterns of the police trojan, which only becomes active within very few processes, are too atypical. And programs like Skype aren't among the typical targets of such malware as ZeuS or SpyEye. If at all, a virus scanner is probably most likely to become suspicious during the execution of the trojan's installation routine. This wouldn't really help if the trojan is installed during a customs inspection – which is what happened in the only documented case![]() so far. During such an inspection, the customs official could, if necessary, even add the spyware to the AV software's exceptions list. The most successful protection in this scenario would probably be to fully encrypt the notebook with pre-boot authentication.
so far. During such an inspection, the customs official could, if necessary, even add the spyware to the AV software's exceptions list. The most successful protection in this scenario would probably be to fully encrypt the notebook with pre-boot authentication.
Government trojans can't really be compared with malware that is deployed on a large scale anyway. They are far more similar to the customised products that are used for breaking into and spying on specific companies. Such spyware products are developed for a specific purpose and will never be deployed on a large scale. Against these threats, AV software provides a similar level of protection – virtually none. The signatures that have now been issued are more of a fig leaf than a shield. Those who want to ensure that such digital snooping products don't violate their digital privacy, as defined by the German Constitutional Court![]() , shouldn't rely on technology and should rather push for political consequences.
, shouldn't rely on technology and should rather push for political consequences.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








