
iOS 6 closes configuration hole
By Ronald Eikenberg
Even users who aren't interested in the new features in iOS 6 should make sure that they install the new version on their iPhone or iPad: the update also closes a critical vulnerability in the code for checking certificates that potentially enables attackers to access the information stored on an iOS device and allows them to intercept data traffic.
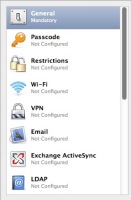
![]() The iPhone configuration program is a powerful tool that can turn into a weapon in the wrong hands
Hardly anything on Apple's web site points towards the existence of the "iPhone Configuration Utility" (Windows, Mac); it can only be found in the support area for enterprise customers. It allows custom system settings to be deployed to multiple iOS devices, for example, it offers a convenient way for companies to deploy their corporate Wi-Fi network settings on devices when supplying their employees with new phones or to implement security guidelines such as a minimum password length.
The iPhone configuration program is a powerful tool that can turn into a weapon in the wrong hands
Hardly anything on Apple's web site points towards the existence of the "iPhone Configuration Utility" (Windows, Mac); it can only be found in the support area for enterprise customers. It allows custom system settings to be deployed to multiple iOS devices, for example, it offers a convenient way for companies to deploy their corporate Wi-Fi network settings on devices when supplying their employees with new phones or to implement security guidelines such as a minimum password length.
Of course, these profiles also offer many opportunities for misuse. Because of this, iOS checks whether the exported configuration files (.mobileconfig) were signed with the certificate of a trusted issuer. In corporate environments, this enables employees to make sure that a pending system update has indeed been approved by the IT department. If the certificate check is successful, iOS confirms this by ticking a box and displaying the word "Verified" in large green letters.
However, the displayed trustworthiness may be ill-founded: as discovered by The H's associates at heise Security when researching a series of articles for c't magazine in Germany, these configuration profiles can be signed on behalf of any person or company – even Apple. The problem also affects the security of private users who usually don't even know that these configuration profiles exist. As most of the displayed text can be easily edited, attackers have almost limitless possibilities.
For example, the profile could look like a mandatory system update from the network provider:
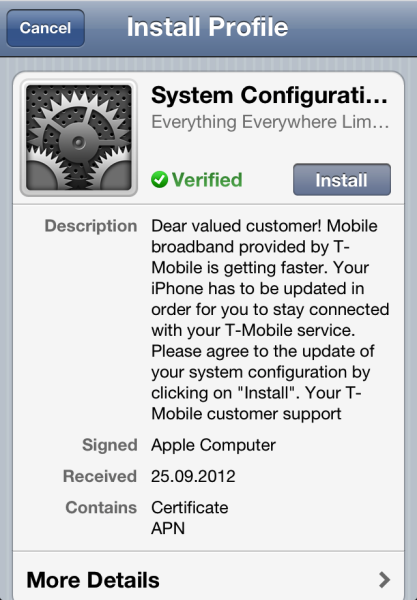
![]() Would this dialog make you suspicious?
Would this dialog make you suspicious?
Configuration profiles such as these may lurk anywhere: attackers could, for example, attach one to an email that appears to have been sent by the mobile network's customer support department. Even when browsing the web, such a dialog may open without any user interaction, and all the accessed web page needs to do is redirect to a configuration file that is hosted online.
Our profile appears to originate from Everything Everywhere Limited and has been "Verified". It was signed by Apple. There isn't really any reason to suspect any tampering – and yet the information is completely bogus. Those who click to confirm this dialog will unwittingly add a proxy to their network settings. Any future data traffic will be routed through this proxy, and whoever operates the proxy will be able to read any data that is sent or received.








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








