Rapid relief for osCommerce administrators
by Jürgen Schmidt
osCommerce systems are currently being targeted by a mass hacking attack – online shop administrators need to act immediately. This article aims to help administrators to help themselves.
Most of the alerts regarding the mass infection of osCommerce shops merely recommend updating to the latest version, 2.3.1. Unfortunately, performing this upgrade is anything but trivial. In many cases it essentially boils down to setting up the whole shop again from scratch. Even the database format has changed, with the result that a dump of an old version can't be used without substantial spadework.
All of which costs time, but with the danger acute, a rapid reaction is required. This short guide has been put together to help users to check whether their osCommerce system is vulnerable, to check whether they have been infected and to apply a workaround to provide at least temporary security.
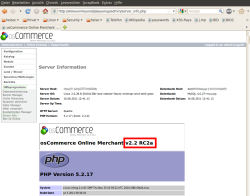
![]() This version of osCommerce is vulnerable
This version of osCommerce is vulnerable
0. Version check
The current wave of attacks is primarily affecting osCommerce versions prior to 2.3.0, in particular all 2.2.x versions. Users can check which version they are running by selecting 'tools/server info' from the administrator interface (.../admin/server_info.php). If the version number is 2.3.0 or later, there is no acute danger at present.
1. Checking for infection
Before setting about ensuring that the server is secure, it is worthwhile checking that it has not already been compromised. This can be reliably determined by copying all folders containing the web shop installation files to a local system via FTP. This copy can then be compared to a recent, but hopefully still sound, backup. Under Linux, the command
# diff -w -q webshop/ webshop-backup/
displays a list of files which differ between the two directories or are present in only one. These should then be examined one by one. Particular suspicion should fall on any commands which embed an iframe within the web site. There is a simple way to search for this string in the web shop directory:
# grep -R -i "iframe" webshop/
This should find just one harmless instance in a list in a JavaScript file. Users should not, however, rely only on this search, as there are a number of techniques for obfuscating this string – for example by splitting it into parts for reassembly down the line. Checking for both of these two procedures is advisable. The Armorize blog offers a detailed analysis of the current attacks. (The sample code executed on this web page can, however, cause anti-virus software to sound a false alarm, as it detects a false positive.)
If the system has indeed been compromised, it is advisable to restore from a full backup. Alternatively, an attempt can be made to remove the injected code manually, but care is required to ensure that nothing is overlooked.
2. Temporarily securing the site
The current attack is directed at the inadequately secured admin interface in osCommerce 2.2. There are two ways of making it secure; for extra security both can be used.
a) Admin patch
osCommerce developer Harald Ponce de Leon confirmed to heise Security that only one of the long list of updates is actually security related. The Administration Tool Log-In Update secures the administration interface against misuse. This requires the addition of three lines of code to the files
- .../admin/includes/application_top.php
- .../admin/login.php
as described in the link above. This adds an additional security prompt. This alone is enough to thwart the attacks described by Armorize. This can be checked by calling a URL such as
/admin/file_manager.php/login.php?action=download&filename=/includes/configure.php
in a new browser session. If the system is properly secured, a login prompt will be displayed. If, instead, a prompt appears asking whether the user wants to download a PHP file (without having previously logged on), then there is still a problem.
b) Protecting directories using .htaccess
It is also possible to block access to the entire admin directory by creating an .htaccess file. This causes the password to be requested the first time an attempt is made to access the administrator interface during a browser session. This check is performed by the web server itself and is independent of the shop software's own login prompt. This is a somewhat belt and braces approach, but is all the more secure for it. The two articles Authentication, Authorization and Access Control on the Apache web site, and Apache .htaccess micro-howto on CSOFT.net, explain how to create an .htaccess file and how it works.
3. Plan an upgrade
The above measures will allow time to plan a course of action in peace. The shop should now be immune to the current wave of attacks. osCommerce version 2.3.1 includes a range of security enhancements and bug fixes, and for this reason an upgrade is definitely recommended. The major release version 3.0 is a complete rewrite requiring PHP 5.3 or later.
Please note that The H is not able to offer any assistance with further questions on osCommerce. If you are experiencing problems upgrading osCommerce or do not understand something in this short guide, please post a question on The H Security forum, and maybe we or other readers will be able to assist. osCommerce also has its own Security Support Forum.








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








