
Detecting CSRF vulnerabilities
Vulnerability scanning with the OWASP CSRFTester
by Stefan Schurtz
When a malicious web page reconfigures a router or sets up forwarding in a webmail frontend, the culprit is usually a cross-site request forgery. OWASP's CSRFTester hunts down this kind of vulnerability.
A cross-site request forgery – CSRF or XSRF for short – is a technique for indirect attacks, similar to cross-site scripting (XSS). The victim's browser reflects the attack. CSRF takes advantage of URLs that trigger certain events – like logging out of a session:
http://192.168.0.1/session.html?action=logout
or even changing a password. Malicious web sites can then use these URLs to manipulate a victim's system in a specific way. As a minimum requirement for this to work, the user must be logged in to the web application or be able to bypass its password protection. Just recently, DNS entries for more than 4 million routers were manipulated this way so the criminals could do as they pleased with the owners' online banking accounts.
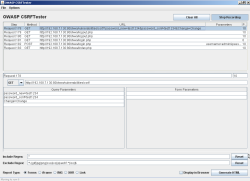
![]() CRSFTester's Java interface is plain but does what it is supposed to
With the Java-based CSRFTester from the Open Web Application Security Project (OWASP), web applications can be easily tested for such vulnerabilities. Basically, it records a legitimate user session and then uses it to build web sites that try to trigger the same actions again.
CRSFTester's Java interface is plain but does what it is supposed to
With the Java-based CSRFTester from the Open Web Application Security Project (OWASP), web applications can be easily tested for such vulnerabilities. Basically, it records a legitimate user session and then uses it to build web sites that try to trigger the same actions again.
CSRFTester is relatively easy to use. Once the archive is unpacked, it can be started up using run.bat and entered in the browser as a proxy (by default, the program does its eavesdropping on port 8008), at which point web sites can be called up and used as normal.
Only when the tool is activated with "Start Recording" in the top right corner does it actually begin to record the URLs retrieved in the browser – including GET and POST parameters, of course. Afterwards, clicking on "Generate HTML" creates the code that will look for CSRF vulnerabilities. The output can be found in a file named "index.html" in a directory of the user's choosing. Five different report methods are available for embedding the proof-of-concept (PoC) code: "Forms", "iFrame", "IMG", "XHR" and "Link".
CSRFTester also includes a variety of filters and ways to process the PoC afterwards. Anyone interested in learning more about cross-site request forgeries or checking their web applications for CSRF vulnerabilities should take a look at this helpful, practical tool that is both quick and easy to use.
It has already served me well in searches for vulnerabilities both during and outside of work. As just one example, I used it to find a number of CSRF vulnerabilities in Deutsche Telekom's T-Online webmail frontend that could have allowed a potential attacker to deactivate the spam filter and forward all of a user's emails to another account. T-Online fixed the problems after The H's associates at heise Security passed the information on to them.
OWASP's CSRFTester is made available as open source under the LGPL licence. Source code for CSRFTester is hosted on Google Code.








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








