Sandbox applications quickly with KVM or LXC
![]() Virt-Sandbox quickly opens applications in a sandbox
In the "Building application sandboxes on top of LXC and KVM with libvirt" FOSDEM presentation, Red Hat developer Daniel Berrange introduced libvirt-sandbox, which confines individual applications in a secured area ("sandbox") using the KVM (Kernel-based Virtual Machine) virtualisation solution or LXC (Linux Containers).
Virt-Sandbox quickly opens applications in a sandbox
In the "Building application sandboxes on top of LXC and KVM with libvirt" FOSDEM presentation, Red Hat developer Daniel Berrange introduced libvirt-sandbox, which confines individual applications in a secured area ("sandbox") using the KVM (Kernel-based Virtual Machine) virtualisation solution or LXC (Linux Containers).
In the KVM variant, the program starts the kernel and initramfs in a virtual machine (VM), which launch the application after booting. With plan9fs (p9fs/plan 9 filesystem), the kernel can read some of the areas of the host filesystem from the VM, making installation of an operating system in the VM unnecessary. According to Berrange's calculations, starting such a VM delays application startup by only about three seconds. This approach shouldn't lead to any significant performance losses when accessing the CPU; for accessing devices, Berrange says, it is possible to achieve about 90% of the performance that would normally be available for an application running directly on the host.
In the LXC variant, the applications run under the host kernel in a separate area, as in container virtualisation; users can visualise this solution as a kind of better secured change root (chroot), which, in the case of libvirt-sandbox, can also read parts of the host system so that no operating system needs to be installed in the container. Setting up a container with libvirt-sandbox apparently takes less than 200 milliseconds, and applications are said to work with virtually no performance loss.
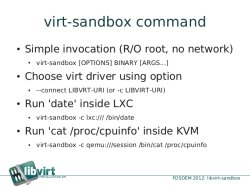
The "virt-sandbox" tool can be used to set up the areas relatively easily so that users hardly even notice that, for example, a VM is being started with KVM. During setup, users can determine whether, and which, network resources are accessible in the sandbox. Berrange offers examples of reasons for using the two approaches: virtually hosting a server application (Apache, etc.), processing untrustworthy multimedia streams, and building RPM packages. Web browsers can also be isolated in the sandboxes to, for example, separate online banking from other internet activity; VNC and Spice can be used to transfer monitor display output from the VM to the host.
SELinux provides additional protections; since 2009, the security framework has been able to use the SELinux Sandbox to confine applications in a separate area, although Berrange says that this approach is problematic for some use-cases and is not very flexible. More information on libvirt-sandbox can be found in the email announcing the first public release, in the slides for the FOSDEM presentation and in a blog post in which Berrange provides a more detailed explanation. Further information is also provided on the Features page for Fedora 17, which should include libvirt-sandbox and be released in May.
(crve)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















