Flashback trojan exploits unpatched Java vulnerability
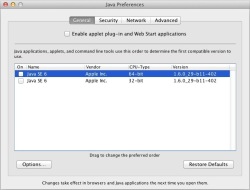
![]() Mac users can find the Java Preferences app under Utilities in the Applications folder
A new variant of the Flashback malware has emerged which is able to install itself on Macs when a user visits an specially crafted website. In an advisory, security specialist F-Secure says that the malware, designated OSX/Flashback.K, exploits a long-known Java SE 6 vulnerability (CVE-2012-0507). The vulnerability was fixed in the Windows versions of Java SE (6 Update 31 and 7 Update 3) back in February, but the current official Java update from Apple is based on Java SE 6 Update 29 and dates back to November.
Mac users can find the Java Preferences app under Utilities in the Applications folder
A new variant of the Flashback malware has emerged which is able to install itself on Macs when a user visits an specially crafted website. In an advisory, security specialist F-Secure says that the malware, designated OSX/Flashback.K, exploits a long-known Java SE 6 vulnerability (CVE-2012-0507). The vulnerability was fixed in the Windows versions of Java SE (6 Update 31 and 7 Update 3) back in February, but the current official Java update from Apple is based on Java SE 6 Update 29 and dates back to November.
Mac users can protect themselves from the trojan, which is able to download code from the web and modify the way that some web sites are displayed, by disabling Java via the Java Preferences tool (Applications ➤ Utilities ➤ Java Preferences). According to F-Secure, OSX/Flashback.K asks the user to enter the administrator password at one point during the installation process, but attempts to install itself even if the user declines to enter it. The security company also provides instructions how to detect an existing infection. It is not yet clear how widely distributed OSX/Flashback.K is.
See also:
- Critical Java hole being exploited on a large scale, a report from The H.
(crve)
![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)
















