Worm manipulates databases in Iran
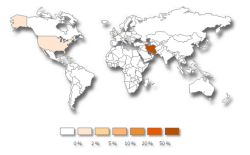
![]() The malware infects mainly computers in Iran. Users in the UK and the US are largely unaffected
The malware infects mainly computers in Iran. Users in the UK and the US are largely unaffected
Source: Symantec
Security firm Symantec has discovered a specialised worm called W32.Narilam that can compromise SQL databases. Symantec reports that the malware "speaks" Persian and Arabic and appears to target mainly companies in Iran. Narilam is, therefore, reminiscent of Stuxnet and its variants.
Narilam spreads via USB flash drives and network shares. Once inside the system, the worm searches for SQL databases that are accessible via the Object Linking and Embedding Database (OLEDB) API. Rather than steal found target data for intelligence purposes, the worm proceeds to modify or delete the data and can, says Symantec, cause considerable damage. Stuxnet similarly served no intelligence purpose and was designed to sabotage its target – an uranium enrichment facility in Natanz, Iran.
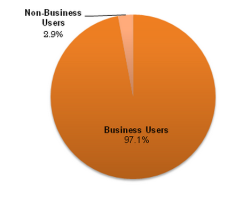
![]() Narilam affects almost exclusively "corporate users"
Narilam affects almost exclusively "corporate users"
Source: Symantec
The purpose of Narilam, or that of the worm's authors, remains unknown. However, Symantec says that its analysis suggest that the saboteurs appear to have targeted corporate data records. Apparently, the worm's translated instructions include object names such as "sale", "financial bond" and "current account". Due to the malware's level of specialisation, Symantec rates the infection risk as low. The security firm notes that current analysis results indicate "that the vast majority of users impacted by this threat are corporate users."
Some of the worm was written in the Delphi programming language. Symantec says that the worm takes its name from its own attributes, because it searches for SQL databases with three specific names: alim, shahd and maliran.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








