Windows exploit protection mostly unused
![]() More than half of the analysed applications use neither of the Windows security functions.
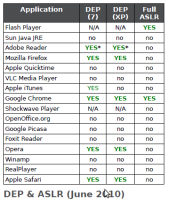
According to an analysis by security firm Secunia, very few applications use the Data Execution Prevention (DEP) and Address Space Layout Randomisation (ASLR) features of Windows which can render attacks on vulnerabilities ineffective. In total, the company looked at 16 popular applications such as browsers, media players and office applications.
More than half of the analysed applications use neither of the Windows security functions.
According to an analysis by security firm Secunia, very few applications use the Data Execution Prevention (DEP) and Address Space Layout Randomisation (ASLR) features of Windows which can render attacks on vulnerabilities ineffective. In total, the company looked at 16 popular applications such as browsers, media players and office applications.
DEP prevents attackers from executing the code they have injected into the stack or heap via a buffer overflow – it can't prevent the overflow itself. However, attackers don't necessarily execute their own code there and then. They often use a manipulated return address to jump to a code segment that has already been loaded by the application. Attackers usually try to jump to specific C library functions (return-into-libc attack).
As the functions are typically loaded into the same memory locations, the attackers know where to direct their code. The ability to predict this is what ASLR is designed to impede. Windows 7 and Vista choose a random memory address when loading the code of a process, the pertinent DLLs, the stack and the heaps. Although this can also be bypassed using certain tricks, it still makes exploits less reliable – and attackers often only have one shot.
Windows leaves it up to each application to set specific flags when loading and to signal that DEP and ASLR should be used. While most Microsoft applications frequently use these functions, Secunia say that third-party applications either don't use them at all or implement them only partially or in the wrong way. The Firefox, Opera and Safari browsers, for instance, only support DEP, but not ASLR. Only Google's Chrome web browser uses both options.
Media players such as Winamp, RealPlayer, QuickTime and VLC use neither option. In mid-2008, Apple already advertised that they had implemented an ASLR-based "Exploit Prevention mechanism" (XPM) in QuickTime. However, a closer look revealed that ASLR continues to be disabled for numerous QuickTime libraries and applications.
According to Secunia, the infrequent use of these options is likely to be another reason for virus authors to target more applications by vendors other than Microsoft.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








