When the neighbour's wireless router sounds the attack
When thinking about viruses, worms and trojans, we usually think of the internet. But now scientists of Indiana University and of the Institute for Scientific Interchange (ISI) in Italy have investigated wireless networks as a potential platform for the distribution of worms, and have developed an epidemic model depicting how fast such a WiFi worm might spread across a city.
Wireless routers are especially interesting in this context. They are usually switched on permanently, are available to anyone and have become very popular. Although all models offer security features to protect them from unauthorised access, these features are often not activated by the user, or can be bypassed with very little effort. In the surveyed cities of Chicago, Boston, New York City, San Francisco Bay Area, Seattle and Indiana, the researchers estimate that only 20 to 40 percent of wireless routers operate with cryptographic features such as WEP or WPA enabled. These cities were selected because the public Wireless Geographic Logging Engine (WiGLE) provides sufficient data about the wireless networks available there. According to the WiGLE maps, it is already difficult to find a WiFi-free zone in areas like Manhattan.
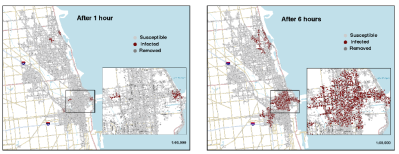
![]() A WiFi worm could infect hundreds of WLAN routers within a very short time.
A WiFi worm could infect hundreds of WLAN routers within a very short time.
Even with cryptographic features enabled, protection is by no means one hundred percent assured. WEP only represents a small hurdle and can be cracked with tools such as aircrack-PTW within a short period of time. Once this hurdle has been overcome, the router's access password needs to be guessed. The research suggests that users often leave their routers' default passwords in place. But even if the password were to be changed, the researchers estimate that it can be cracked in a maximum of 65,000 attempts (the size of the dictionary) in 25 percent of cases. Via the update feature, the worm can then be written into or even replace the firmware, and can then spy out further routers in its vicinity. All that the WiFi worm requires for this task is already available as packages in the OpenWRT Open Source router distribution: kismet, aircrack-NG/PTW etc.
The epidemic model developed by the study's authors - Hao Hu, Steven Myers, Vittoria Colizza and Alessandro Vespignani - suggests that several tens of thousands of routers could be infected with a worm within two weeks, most of them even within two days. To avoid the potential distribution of these so far only theoretical flying worms, users should be forced to change the default password of their router's configuration interface and to enable WPA functionality with passwords which cannot be guessed.
The variety of different router models it would encounter while it spreads might also inhibit a worm's distribution. However, the model used in this study did not include that parameter. To infect a WLAN router successfully, a WiFi worm would have to have specific firmware for each individual model. Even under the uniform OpenWRT platform there are numerous images for the various models.
See also:
* WiFi Epidemiology: Can Your Neighbors’ Router Make Yours Sick? ![]() , study by Hao Hu, Steven Myers, Vittoria Colizza, Alessandro Vespignani
, study by Hao Hu, Steven Myers, Vittoria Colizza, Alessandro Vespignani
(mba)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








