Unpatched security holes: IBM re-evaluates
![]() Unpatched holes? In the updated table, Google no longer has any.
Unpatched holes? In the updated table, Google no longer has any.
Source: IBM
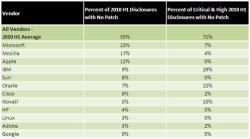
IBM's X-Force security team has updated the security report for the first half of 2010 it released last week after two vendors questioned the correctness of the team's evaluations. The controversy was sparked by a table containing the ten vendors who left the most security holes unpatched over a period of six months: Ranking in the top 10 for the first time, Google was originally said to have left 33% of its critical holes unpatched, which put the vendor in first place in this category.
However, according to Google's own research, the 33% result was caused by one of three critical holes – and even that only because the allegedly unpatched hole was classified incorrectly. Google said that a "stack buffer overflow" is only a "stack overflow" and can potentially be exploited to destabilise a system, but not usually to inject malicious code. This decreases Google's unpatched critical holes from 33% to 0%.
As a consequence of the vendor feedback, IBM has re-evaluated all the collected data used to generate the table figures: The updated version of the table consequently also shows Linux (previously 20%) and Sun (previously 9%) with no unpatched critical holes. Apple's 0% already set an example in the first version. Microsoft was the only vendor whose figures had to be adjusted upwards: from 7% to 11% now.
This is further proof that studies of this kind can at best provide pointers and should never be used as the only decision-making criterion. That studies have to be treated with caution is commonplace – but rarely do those who create them have to make such drastic corrections. Another well-known example is Verizon: In this year's Data Breach Investigations Report, the vendor had to correct a crucial statement made in the previous report. Verizon had been too quick to say that the times when corporate data breaches were mainly caused by internal sources are over.
See also:
- Verizon claims full disclosure is the preserve of narcissistic "pimps", a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








