Twitter fails to block Cross Site Scripting flaw
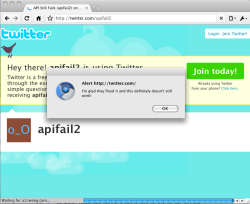
![]() The dialog popped up by @apifail2
A vulnerability in the way Twitter handles the URL of client applications that post to the microblogging service can allow for cross site scripting attacks. Twitter maintains an index of client applications that are able to post messages to Twitter that authenticate with OAuth. This allows developers to register an application name, description and URL of their application and when Twitter messages posted by their application are viewed on the web, the application name is displayed as a link to the application URL underneath each message. David Naylor, a UK based SEO expert, discovered that the URL field was unfiltered and demonstrated the problem. In comments on Naylor's blog, a Twitter representative says that the problem has been patched.
The dialog popped up by @apifail2
A vulnerability in the way Twitter handles the URL of client applications that post to the microblogging service can allow for cross site scripting attacks. Twitter maintains an index of client applications that are able to post messages to Twitter that authenticate with OAuth. This allows developers to register an application name, description and URL of their application and when Twitter messages posted by their application are viewed on the web, the application name is displayed as a link to the application URL underneath each message. David Naylor, a UK based SEO expert, discovered that the URL field was unfiltered and demonstrated the problem. In comments on Naylor's blog, a Twitter representative says that the problem has been patched.
Naylor, after finding his demonstration account had been disabled, checked the issue with a new demonstration account (since also disabled) and found that, rather than filtering the field for HTML elements and ensuring it was a valid URL, Twitter's developers had just filtered the URLs on spaces. This allowed the exploit to continue working as he was able to craft a new application URL which pops up an alert in the browser on the Twitter account @apifail2. Naylor says that this could be maliciously exploited and lead to spamming or credential theft if left uncorrected, and suggests users use a desktop Twitter client as they are not generally vulnerable to this attack. Twitter has now closed the @apifail2 account.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








