Trojans conceal themselves using instant messaging protocols

Trend Micro has discovered new trojans which camouflage their communication by imitating common instant messaging protocols such as Windows Live Messenger or Yahoo Messenger. The security company has dubbed the trojans "Fakem RATs" (a RAT being a remote access trojan). They allow attackers to remotely sort through folders on a victim's computer, take screenshots, control webcams and microphones and access data.
The company has reported that, since 2009, some malware has been concealing its data traffic by mimicking known instant messaging protocols or, to avoid detection, trying to camouflage its data traffic as HTTP or HTTPS. To achieve this, these trojans copy at least the header of the instant messaging protocol, leaving the remainder of the packets to carry the trojan's encrypted communications.
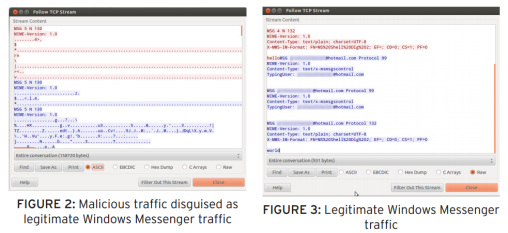
![]() Traffic analysis of a trojan trying to camouflage its communications as Windows Live Messenger traffic
Traffic analysis of a trojan trying to camouflage its communications as Windows Live Messenger traffic
Source: Trend Micro
The trojans are not spread over the chat systems but instead spread using email and typical social engineering techniques. The malware infects systems using specially crafted Word and Excel files which exploit vulnerabilities in Microsoft Office (CVE 2009 3129, CVE 2010 3333, CVE 2012 0158). The vulnerabilities in question have since been patched. The company discovered the malware's capabilities by allowing attackers to use it to infect a honeypot system and examining the results.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








