Tool to track security-sensitive changes to Windows
 Microsoft has announced the free Attack Surface Analyzer tool, designed to highlight any changes to a Windows system that are introduced when installing a program. According to Microsoft, the tool displays any added files, registry keys and ActiveX controls and points out open server ports. It is also said to evaluate the access privileges configured for the added files.
Microsoft has announced the free Attack Surface Analyzer tool, designed to highlight any changes to a Windows system that are introduced when installing a program. According to Microsoft, the tool displays any added files, registry keys and ActiveX controls and points out open server ports. It is also said to evaluate the access privileges configured for the added files.
The tool mainly aims to enable developers to establish the extent to which a program has increased the attack surface on a Windows PC. However, it generally also allows administrators and end users to find out whether installing a certain program has negatively impacted system security, although it does not examine the installed software for concrete vulnerabilities. A beta version of the tool has now become available for download.
![]() Not particularly critical, but avoidable: ICQ has apparently misconfigured the access privileges for the installed files.
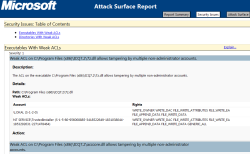
To generate a report, the tool needs to scan a system before and after the program in question is installed. In a brief test by our associates at heise Security with Messenger ICQ under Windows 7, Attack Surface Analyzer pointed out that the access privileges for numerous installation files were too comprehensive, apparently allowing non-administrators to manipulate these files; this could potentially enable an attacker with restricted access privileges to pass on malicious code to another user of the same PC (with a different account).
Not particularly critical, but avoidable: ICQ has apparently misconfigured the access privileges for the installed files.
To generate a report, the tool needs to scan a system before and after the program in question is installed. In a brief test by our associates at heise Security with Messenger ICQ under Windows 7, Attack Surface Analyzer pointed out that the access privileges for numerous installation files were too comprehensive, apparently allowing non-administrators to manipulate these files; this could potentially enable an attacker with restricted access privileges to pass on malicious code to another user of the same PC (with a different account).
The announcement of the tool was timed to coincide with the Black Hat security conference. At this conference, Microsoft has also introduced the updated version 1.2 of the BinScope Binary Analyzer tool, which supports Visual Studio 2010. BinScope Binary Analyzer examines binary code to establish whether all the recommended and required security flags (such as /GS and /SafeSEH) as well as protective mechanisms and checks (such as /DYNAMICBASE for ALSR) are available and enabled in the software.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








