Thousands of web pages manipulated in large-scale scareware attack
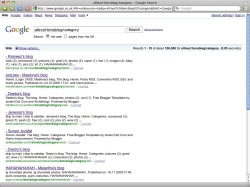
![]() These 106,000 results lead to malware. Don't click the links.
In a post on its company blog, security firm Cyveillance reports on a large-scale scareware attack which appears to have involved manipulating more than 200,000 harmless web pages (for additional information about scareware read our feature article "Thieves and charlatans - Rogue antivirus products" in The H Security channel). Google's search engine reportedly plays an important role in the attack, pointing users to the compromised web pages when certain search terms are entered. According to the report, the search terms used in the attack are not the usual suspects, such as "Britney Spears", "Obama" or "Paris Hilton". Google apparently only provides links to the infected pages when a longer combination of words is entered.
These 106,000 results lead to malware. Don't click the links.
In a post on its company blog, security firm Cyveillance reports on a large-scale scareware attack which appears to have involved manipulating more than 200,000 harmless web pages (for additional information about scareware read our feature article "Thieves and charlatans - Rogue antivirus products" in The H Security channel). Google's search engine reportedly plays an important role in the attack, pointing users to the compromised web pages when certain search terms are entered. According to the report, the search terms used in the attack are not the usual suspects, such as "Britney Spears", "Obama" or "Paris Hilton". Google apparently only provides links to the infected pages when a longer combination of words is entered.
The criminals exploit the circumstance that, surprisingly, most of the queries entered in Google apparently contain four to five words. According to Cyveillance, they have seemingly found a successful "niche". To get Google to index the word sequence, the criminals install their own blog on the hacked pages and automatically generate entries whose headings contain the required words (for example "las vegas rental no credit check", "real world melinda and danny" or "uninvited song lyrics alanis morrissette").
While Google's search results usually warn of such specially crafted web pages, this is only the case if a link leads directly to the page. When a link is redirected to a malicious page, there is no alert in the search results.
Victims who have arrived on one of the pages are redirected to one of the criminals' servers, which will pretend to scan the hard disk for viruses and then attempt to trick the user into paying for and downloading bogus anti-virus software by presenting fake malware infestation results. However, the redirect only becomes active if the user arrived at the page by following a Google search result. For this purpose, the injected blog software checks the HTTP referrer.
The criminals' server domains are all reported to be registered with the Chinese TodayNIC.com registrar and are also said to be involved in spreading the Koobface worm for Windows. How the criminals hack the pages has not been fully clarified. A vulnerability in the old version 1.4.24 of the Coppermine photo gallery software is said to play a role in some cases.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








