TETRA digital radio - now for everyone
 At the last PH-Neutral hacker conference, award-winning open-source hacker Harald Welte not only presented the basics behind Terrestrial Trunked Radio (TETRA), but also conjured up some open source software that can be used to receive, record, and decode digital radio.
At the last PH-Neutral hacker conference, award-winning open-source hacker Harald Welte not only presented the basics behind Terrestrial Trunked Radio (TETRA), but also conjured up some open source software that can be used to receive, record, and decode digital radio.
In principle, TETRA is a lot like the GSM mobile communications standard for cell phones but differs so much that you cannot reasonably recycle any of the existing GSM software and hardware. TETRA is designed to provide a common basis for digital radio communications in Europe for fire departments, emergency services, and the police, along with airports, energy providers, and public transport firms.
The standard therefore contains a wide range of security functions, such as encryption, authentication and so on – all of which should really be taken for granted in this field. But there is a common problem with these functions; the security measures are "optional" in standard settings. Because implementation costs money, although state authorities (such as the police) encrypt their radio communications, almost all private-sector radio networks forgo the expensive security extensions and send their radio signals as plain text with cheap devices and a simple infrastructure.
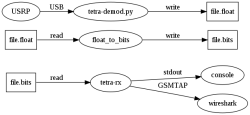
![]() At present, radio signals received can be decoded in several steps. A Wireshark module eventually produces audio files from the recordings.
At present, radio signals received can be decoded in several steps. A Wireshark module eventually produces audio files from the recordings.
Source: Osmocom TETRA
A small USB receiver, such as a Funcube dongle, can be inserted into a notebook, and software, like the OsmocomTETRA presented by Welte, could then be used by anyone to receive and listen to the TETRA radio communications of utilities and public transport providers. Insiders say that unknown parties have already done so, for example to record conversations between tram drivers and the control centre at Berlin's BVG public transport service, creating audio files that can be played back on any PC in the process.
Although sniffing around in third-party TETRA networks is not likely to become a popular sport – courts are likely to interpret such actions as criminal behaviour – Welte hopes that more security experts will deal with the new protocols. "Too many IT security people are still dealing with TCP/IP security even though there are a lot more communications systems", he told The H’s German associates at heise Security. Over the past few years, Harald Welte has himself developed security tools for RFID (openpcd.org), DECT (deDECTed.org) and GSM (OpenBSC, OSmocomBB). OsmocomTETRA is the latest addition to his collection.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








