Stuxnet 0.5: The sabotage worm is older than previously thought
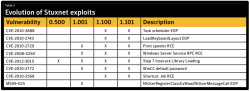
![]() Further infection vectors were incorporated into Stuxnet over time
Further infection vectors were incorporated into Stuxnet over time
Source: Symantec
The first Stuxnet worm was in operation as early as 2007, not just, as previously believed, since 2009. Security firm Symantec found the older variant during a routine check of its malware database and then analysed![]() the version as Stuxnet 0.5. The discovery means that the history of Stuxnet will need to be rewritten.
the version as Stuxnet 0.5. The discovery means that the history of Stuxnet will need to be rewritten.
Apparently, the older Stuxnet worm was circulated to disrupt the Iranian nuclear programme before 15 November 2007; on that day it was uploaded to Virus Total for testing. However, one of the associated command & control (C&C) servers was reportedly registered on 3 November 2005.
The early variant was less aggressive and only used one deployment pathway after successfully infecting a system – 0.5 could only be transmitted via Siemens Step 7 project files, which are usually only exchanged by developers. This could be one of the reasons why Stuxnet 0.5 wasn't detected earlier. Later versions included 0-day exploits that targeted holes in Windows.
Like later versions, however, 0.5 targeted the centrifuges in uranium enrichment plants and manipulated Siemens Programmable Logic Controllers (PLCs) to do so. Apparently, Stuxnet 0.5 particularly targeted valve controls to manipulate the distribution of uranium hexafluoride gas. Its presumed aim was to increase pressure in the centrifuge cascades fivefold in order to destroy the components.
Version 0.5 used eight consecutive steps. At first, it lay dormant for a while in the system to record normal system operations and measurement results. Then, it started to manipulate the centrifuge valves while presenting the older results to local engineers in order to disguise the pressure increase.
According to a report by Wired magazine, inspections by the International Atomic Energy Agency (IAEA) in Iran found, for instance, that the centrifuge cascades' productivity plunged repeatedly between January and August 2007 although the number of centrifuges kept being increased. Apparently, engineers were also busy replacing centrifuges when the inspectors visited. The decreased productivity is believed to have been caused by Stuxnet 0.5.
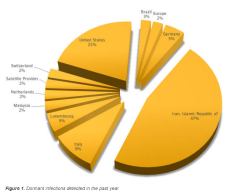
![]() Stuxnet 0.5 remains active in certain places. Symantec's analysis of its activity during 2012 demonstrates the widespread distribution
Stuxnet 0.5 remains active in certain places. Symantec's analysis of its activity during 2012 demonstrates the widespread distribution
Source: Symantec
That Stuxnet 0.5 was soon to be replaced by later versions is demonstrated by further data. The worm was programmed to not infect any additional systems and to only remain active in previously hijacked machines from 4 June 2009. Communication with the C&C servers was terminated on 11 January 2009.
Apparently, version 0.5 was immediately superseded. In June 2009, variant 1.001 became active – the variant that was long considered to be the first. This version of Stuxnet was able to update older versions and probably covered up further traces of the earlier 0.5 version. More variants followed after 1.001: for example, researchers also identified version 1.100 from March 2010 and version 1.101 from April 2010. The apparent gap from version 0.5 suggests that a considerably greater number of versions were developed but not released into the wild.
Although Stuxnet 0.5 is now a few years old, and although this version was superseded by various updates, Symantec still found a few infections last year; for example, Stuxnet 0.5 is still believed to be active in several German Siemens control systems.
It is thought that, apart from Stuxnet, further malware such as the Flame spying trojan was specially developed by the US and Israel to sabotage the Iranian nuclear programme. At least that's what was indicated on several occasions during the 2012 US election campaign.
(fab)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








