Spied on despite encryption
In order to prevent misuse it is always advisable to use encrypted connections for sensitive activities, like online banking, or reading emails at services like Google Mail. However, in certain circumstances, attackers may still gain access to bank or email account data, despite the encryption.
The technique used is a special form of cookie theft. Although it was already discussed a year ago, it has only now received the attention it deserves – the main reason being that a tool has now become available which allows actual attacks to be carried out.
The problem arises because many services handle session management and sometimes also authentication, via cookies. This isn't detrimental when cookies are exchanged via encrypted https connections. However, encryption can't be guaranteed, as many sites don't mark important session cookies with the security flags that prevent the browser from reusing the cookies for unencrypted connections. As a result, browsers may send cookies via unencrypted connections, which can be spied on when users simply access a normal page at their mail provider's web site.
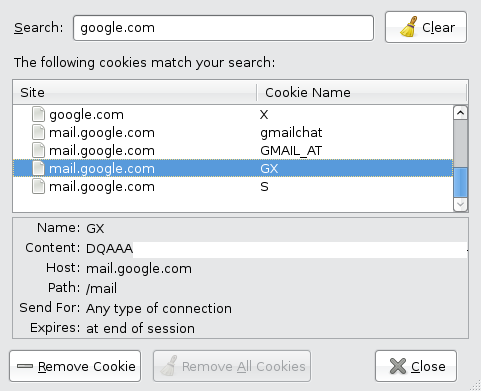
This cookie is all that's required for accessing a mailbox. It is also used for unencrypted connections.
The actual attack can be carried out like this: victims use an encrypted wireless connection to log into a service like Google Mail and read their emails – also encrypted. While still logged in, users then access an arbitrary, non-secure web page. An attacker on the same wireless system, injects this page with a reference to an image, allegedly stored at the unencrypted http://mail.google.com site. The browser tries to retrieve the image, sending the Google Mail cookie to the server in the process – unencrypted. The attacker listens in on this exchange and can subsequently use the cookie to open the user's mailbox at Google Mail.
At the Defcon security conference, Mike Perry demonstrated such an attack and announced that he would release a tool within two weeks. Sandro Gauci appears to have developed the idea at the same time and now not only presents a paper and a video, explaining and demonstrating the details, but even complements his release with a suitable Python script called Surf Jack. Ironically, the script is hosted by none other than Google itself.
The attack can not only be carried out in wireless lans, but also via ARP spoofing, for example in corporate networks, or by poisoning the DNS cache of basically any network. Successful targets are those who use services which authenticate via cookies and whose server does not set the secure flag. According to Perry, these include Google Mail, as well as Facebook and Amazon. Gauci even claims to have found two banks that are vulnerable.
Unfortunately, users normally don't have access to their cookies' security settings. Google, however, recently introduced the option to always use a secure connection for accessing Google Mail. As it happens, this option also causes the server to set the secure flag, exclusively restricting the Google Mail session cookie to encrypted connections. The search engine provider unfortunately neglected to document this measure. As a result, many users already consider their details safe, because they have always accessed their mailboxes exclusively via encrypted connections. Users are advised to enable the respective option in their Google Mail account settings, at their earliest convenience.
(trk)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








