"Sophisticated Android Trojan" identified
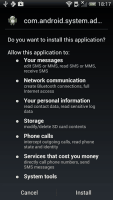
![]() The trojan doesn't have the ability to skip displaying what permissions it needs.
The trojan doesn't have the ability to skip displaying what permissions it needs.
Source: Kaspersky Lab
The researchers at Kaspersky Lab have identified what they call "The most sophisticated Android Trojan" yet. Packaged as an encrypted DEX file with obfuscated code, the malware has been given the name Backdoor.AndroidOS.Obad.a or Obad.a for short. It runs entirely in the background with no user interface, yet sends SMS to premium rate numbers, downloads more malware and distributes it over Wi-Fi and Bluetooth, and remotely performs commands.
Kaspersky found the program set out to defeat typical analysis techniques for Android malware. For example, it exploits an error in the DEX2JAR software to complicate statistical analysis of the trojan and an error in the handling of AndroidManifest.xml so that it does not follow Google standards but still works on devices – this caused problems for dynamic analysis of the code. Another flaw in the Android operating system was exploited to allow 0bad.a to have extended device administrator privileges without appearing on the list of applications which have those privileges – this makes 0bad.a hard to delete from a phone.
According to Kaspersky Lab's analysis, all external methods are indirectly called through Java's Reflection API. This would slow static analysis as it would appear at first glance that 0bad.a wasn't calling anything. Strings undergo decryption at runtime, while the addresses of command and control servers require an internet connection to access a Facebook page, extract a decryption key and use that to further decrypt the address.
Once Kaspersky Lab had overcome the various defences, the 0bad.a malware was exposed as an app which initially asks for device administration privileges, saying it needs to control when the screen is locked on the device. It appears to use this privilege when connected to a free Wi-Fi network or Bluetooth, blanking the screen for up to ten seconds and attempting to copy itself to other devices. 0bad.a also tests for the ability to get super user privileges and sends that information – along with details on whether it has Device Administrator privileges, plus the MAC address for Bluetooth, operator and telephone number, IMEI, account balance and local time – to a C&C server at androfox.com as an encrypted JSON object.
The trojan can then be commanded by the C&C to perform a number of tasks. These include sending text messages, pinging addresses, getting an account balance, acting as a proxy for another operation, connecting to addresses, downloading files from the server, reporting on installed applications or the user's connection data, opening a remote shell or sending files to all detected Bluetooth devices. Another set of commands can be transmitted over the internet but also received through SMS messaging. The SMS commands include the ability to get the trojan to immediately connect to its C&C server, connect to a new C&C server or delete tasks from its database. These commands would be useful if trying to re-take control or hide the trojan network.
Kaspersky Lab doesn't believe that Backdoor.Obad.a is very widespread, seeing it only in 0.15% of malware infection attempts on mobile devices, but they liken it more to Windows malware in how it exploits so many vulnerabilities and is so complex, unlike other mobile malware. That suggests we are passing through an evolutionary phase of Android malware.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








