Some online backup services insecure
Some on-line backup services fail to provide adequate security, meaning attackers can read and even change the data being backed up or restored when it's transmitted over the internet. Tests by heise Security show that four of the six services tested were vulnerable to attack.
While all of the tested systems encrypt communication with the backup server using SSL, external attackers can sniff the access code as plain text by acting as a man-in-the-middle (MITM) if the locally installed backup software does not perform sufficiently rigorous checks on the authenticity of the server's certificates. In the vulnerable systems, we were able to hijack the connection from the client software to the backup servers.
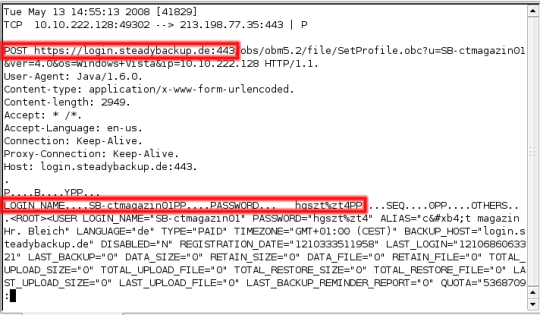
![]() Although login data are transmitted via an encrypted https connection, we could still read it.
Although login data are transmitted via an encrypted https connection, we could still read it.
In our test, we found that external attackers can even get access to all data stored at NTT Europe's Steady-Backup because, with the default settings, the access password is also used to encrypt the data. The consequences could be far-reaching because this service uses backup software developed by Ahsay of China, which claims to be behind more than 100 service providers in Europe alone.
At iDrive, we managed to use the access data we stole to delete the account and its backup data. While the BullGuard client did not transmit any passwords in plain text, instead using hashes, attackers are nevertheless able to take over a session and take various actions, such as deleting files.
While all the services tested employ standard encryption algorithms, which are themselves very difficult to break, the poor authentication used in some means that the encryption can be bypassed simply by setting up a fake backup server with a forged certificate, then using one of a number of techniques to redirect connections from the genuine server to the fake one.
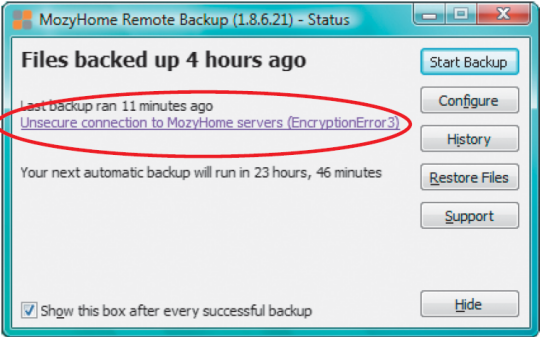
![]() The Mozy client was the only one to warn us about our MITM attack.
The Mozy client was the only one to warn us about our MITM attack.
Only Carbonite and Mozy noticed that the certificate provided during a MITM attack was forged and refused to connect to the fake server. But only Mozy provided valuable information and warned users that they may be under attack. Carbonite simply issued the vague message "Server not reachable due to maintenance".
Although this MITM attack scenario may not be relevant for every customer, the scope of these security problems can hardly be overstated. While companies say they store customer data safely, some of the elementary security measures they take are implemented so carelessly and unprofessionally that they can easily be overcome. Backups are matters of trust, and that does not change when they are made on-line. Those who are sloppy with security here risk losing the long-term trust of their customers. The providers we contacted know this, and all of them have promised to close the holes we discovered.
The complete test results will be published in heise online's German sister publication, c't magazine on Monday, May 26.
(mba)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








