Skype also affected by supposed "Firefox vulnerability"
The ripples from the problematic way special URLs are handled, discovered last week, continue to spread. Research by heise Security showed that as well as Firefox, other applications like Skype or Miranda can act as a gateway for the problem. This strongly suggests that the actual cause of the problem is the confusing way in which Windows handles URLs. If a program considers that it is not responsible for dealing with a URL type such as mailto:, it passes such URLs to the operating system to be dealt with further. Under Windows XP, however, what then happens depends on whether or not Internet Explorer 7 is installed (even if IE has nothing to do with the protocol in question).
Thus URLs such as %00 or a bare percentage character (a % which is not part of a valid escape sequence, such as %FF) can start programs with arguments directly. If a user clicks on a URL of the form
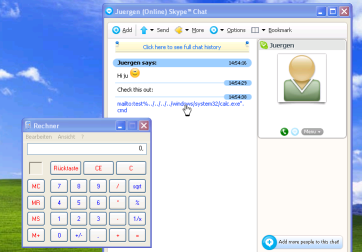
mailto:test%../../../../windows/system32/calc.exe".cmd
in Firefox or a chat window of Skype or Miranda, the calculator is launched – at least it is under Windows XP with IE7. Not, however, under Vista or with the old IE6. Other programs which engage with the URL handling system also affect this behaviour. Which other protocols are affected, besides those already documented (mailto:, news:, snews:, nntp: and telnet:) is not clear. Alternatively users can test this by passing the string directly to the operating system using the "Run" option from the Start menu. Attackers could exploit this behaviour to execute arbitrary commands on a victim's system, which they can either inject using a specially crafted web page or send via a Skype message.
After being informed by heise Security that % also triggers the bug, the Mozilla development team have realised that their initial approach of filtering %00 out of URLs is inadequate. The entry in the bug database states that the bug is "RESOLVED/FIXED", but Mozilla developer Dan Veditz has confirmed to heise Security that the current patch is considered ineffective as % can also trigger the problem.
The developers are currently discussing how they can effectively protect users without unnecessarily hindering legitimate programs. They are, however, faced with the problem that it is still not clear how Windows actually handles URLs. At least there is now some initial information from Microsoft about how Windows handles different URLs.
As reported to heise Security by Dan Veditz, the development team is currently considering whether it should release the almost completed Release Candidate for version 2.0.0.6 without this patch, as it already contains a different patch for a similar problem, namely unfiltered quotation marks, which provoke a nasty reaction in some programs. This would also eliminate all of the known % exploits to date. This would gain the developers time to consider a clean solution to this problem, argues Veditz.
That programs such as Skype and Miranda are also affected, however, makes it clear that it is now definitively down to Microsoft to bring some order to the chaos and straighten out the way Windows handles URLs as quickly as possible. Simply to wait for all other applications to adapt to the current confusion would be a dereliction of responsibility to users.
- Firefox and Internet Explorer 7 still not getting along [Update] by heise Security
- New findings on "Firefox hole" by heise Security
- Microsoft scores points in the security ping-pong with Mozilla by heise Security
- Some schemes with %00 launch unexpected handlers on windows, Bugzilla entry on the problem with %00 and %
- Firefox may not escape quotes everywhere, Bugzilla on the problem with "
(mba)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








