Serious vulnerabilities in QNAP storage and surveillance systems - Update
 Many of QNAP's NAS products are affected by security problems that, when combined, potentially allow remote attackers to execute arbitrary commands on a system at administrator privilege level – at worst, even via the internet. Apart from pure network storage systems, this particularly affects QNAP Security's VioStor video surveillance systems.
Many of QNAP's NAS products are affected by security problems that, when combined, potentially allow remote attackers to execute arbitrary commands on a system at administrator privilege level – at worst, even via the internet. Apart from pure network storage systems, this particularly affects QNAP Security's VioStor video surveillance systems.
The holes were discovered by Tim Herres and David Elze, who work for the Daimler TSS Offensive Security Team. The testers had reported the problems to CERT back in March, but it appears that CERT was unable to find a QNAP Security representative who would respond to its attempts to explain the problem. When the problem still existed two months later, the two testers contacted heise Security. c't magazine's editorial contacts soon managed to find a contact person at QNAP who organised the release of a first patch.
The integrated web server in VioStor and NAS devices makes a range of utility programs available in the cgi-bin/ directory. This directory is password-protected to prevent unauthorised access: when access is attempted, the server will request a user name and password (HTTP Basic Authentication). The problem is that entering basic guest credentials will grant access to the directory, and this functionality can't even be disabled via the user interface.
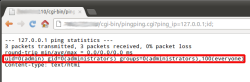
![]() uid=0 proves that a command was executed at root level – in this case on a video surveillance system in Fukushima.
uid=0 proves that a command was executed at root level – in this case on a video surveillance system in Fukushima.
Among the CGI programs that are accessible this way are the create_user.cgi script and, on some systems, pingping.cgi. The former allows potential attackers to create a new admin account (Cross-Site Request Forgery, CSRF), while the ping script enables attackers to inject arbitrary shell commands in such a way that they will directly be executed at root level. Heise Security managed to reproduce this vulnerability.
Scores of vulnerable QNAP systems are accessible on the internet, but the situation in which arbitrary employees can gain access to a company's network storage is likely also undesirable in any enterprise network – not to mention the possibility that, during a break-in, intruders simply need to connect a laptop to a network socket to delete any incriminating video footage from a VioStor surveillance system. According to the Daimler TSS testers, QNAP VioStor network video recorders, at least up to firmware version 4.0.3, are affected. The sensitivity of the problem becomes apparent when we take a look at all the places where these surveillance systems are used: police and military agencies, banks, and others. QNAP's NAS systems also include guest access functionality and, at least when "Surveillance Station Pro" is installed, they also contain the problematic ping script.
CERT has now released an advisory on the matter and rated CVE-2013-0141, CVE-2013-0142 and CVE-2013-0143 at the highest CVSS threat level of 10. QNAP is currently working on the problems and will publish more information soon. Until then users should strictly control access to affected systems. As other CGI scripts have granted access to QNAP systems in the past, it is likely that further potential backdoors are lurking in this directory.
Update 11-06-13 10:40: QNAP has now acknowledged the security problems with its NAS devices. According to the company, only systems that the Surveillance Station Pro application has been installed on are vulnerable. The company recommends that affected users install an update for the application through the App Center or the QPKG Center systems.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








