Security issue in iOS Personal Hotspot
 Security experts at the University of Erlangen-Nuremburg have identified a security issue in iOS's Personal Hotspot feature. The feature, also known as tethering, allows a phone to be used as a hotspot for other devices. A paper from Andreas Kurtz, Felix Freiling and Daniel Metz describes vulnerabilities they discovered in the feature.
Security experts at the University of Erlangen-Nuremburg have identified a security issue in iOS's Personal Hotspot feature. The feature, also known as tethering, allows a phone to be used as a hotspot for other devices. A paper from Andreas Kurtz, Felix Freiling and Daniel Metz describes vulnerabilities they discovered in the feature.
They note that the WPA2 encryption used by default for the Wi-Fi connection is in principle secure, but that this security depends on the encryption password, the pre-shared key, used. If the smartphone operating system issues an insecure default password for Wi-Fi hotspots and users do not modify it to a secure password then, despite a strong encryption algorithm, unauthorised users can gain access to internet sharing on an iPhone or iPad in a matter of seconds.
According to the report, iOS selects an easily remembered password from a list of just 1842 words and supplements this with four random digits. This would theoretically gives rise to around 18.4 million possible combinations, but iOS's algorithm for selecting a word from its dictionary is sloppy and it chooses certain words (e.g. suave, subbed, headed, head and header) with increased frequency. Closer analysis reveals that all 1842 words are to be found in a Scrabble dictionary.
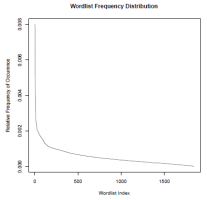
![]() Not only does iOS use a small dictionary, it also selects some words from it conspicuously often
Not only does iOS use a small dictionary, it also selects some words from it conspicuously often
Source: University of Erlangen-Nuremberg
Although the number of possible combinations may at first glance appear large, the paper vividly demonstrates how a single modern graphics card is able to determine the complete password (by simply trying out each word in the order of its probability of occurrence) within just 52 seconds. Windows Phone, on the other hand, gets by without a dictionary and simply selects eight random digits, giving 100 million combinations, requiring a theoretical average of five minutes to crack. Android generates strong passwords, but some modified Android systems, such as HTC devices, are equipped with default passwords such as 1234567890.
To illustrate the security vulnerability, the authors have also released an app, in the form of an Xcode project file, which shows how quickly the password used by an iPhone can be cracked using an optimised dictionary and a cluster of several fast graphics cards.
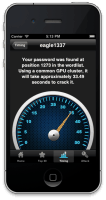
![]() Cracked in seconds [--] the iOS Hotspot Cracker app calculates how long a password would withstand an attack
Cracked in seconds [--] the iOS Hotspot Cracker app calculates how long a password would withstand an attack
Source: Louis-F. Stahl
A future version of the app may enable users to eavesdrop on traffic from other hotspot connections or crack the password. The modest computing power offered by smartphones means that such an attack would take a little longer than the 52 seconds mentioned above, but CPU intensive work could also be outsourced to the cloud, allowing shorter computation times.
To avoid weaknesses in "random passwords", users should therefore always choose a secure password for themselves rather than rely on the password provided by the operating system.
Apple appears to have recognised the problem. The H's associates at heise Security have observed that the latest beta version of iOS 7 suggests random-looking combinations of letters and numbers with a length of at least ten characters for securing mobile hotspots.
(Louis-F. Stahl / sno)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








