Secure Java programming with Fabric
In order to improve the security of applications running on distributed systems, six researchers at Cornell University have developed Fabric![]() . It extends Jif, also developed at Cornell, to add transactions, calls to functions on remote computers and the persistent storage of objects.
. It extends Jif, also developed at Cornell, to add transactions, calls to functions on remote computers and the persistent storage of objects.
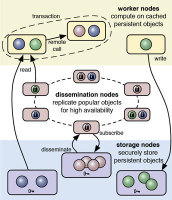
![]() Different types of nodes are involved in the performance of fabric programs.
Different types of nodes are involved in the performance of fabric programs.
Source: cornell.edu
The central idea behind Fabric and Jif is 'principals', which formulate and implement security requirements. Relationships and operators allow users, processes, groups and application-specific units to be modelled each with their own security requirements. Principals can have read or write privileges for objects formulated in 'labels'. int {Alice Bob} x; specifies that the principal Alice controls the variable x and that Bob is able to access its value. The rule {Alice←Bob} permits Bob to change the value of x. During compilation, the compiler checks whether the source code respects access rights to objects. It then generates Java code which is passed to standard Java compilers for further processing.
Multiple processes are involved in executing a Fabric program. Storage nodes manage objects, worker nodes execute the application and dissemination nodes provide copies of objects to reduce the workload of storage nodes. These processes can run on the same machine, usually within a JVM, or be distributed across a network.
Fabric version 0.1 is now available to download (direct tar download link). It requires Java 1.6 and the Apache tool Ant. According to the authors, it should run on all standard versions of Unix.
See also:
- 'Fabric' would tighten the weave of online security, an article from Cornell Chronicle Online.
(trk)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








