Scareware becomes ransomware again
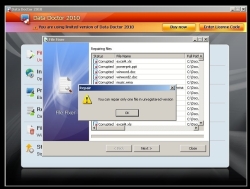
![]() Data Doctor 2010 will allegedly repair files, for a price.
Rather than infected files, the latest scareware uses allegedly corrupted files to alarm users. The setup work is performed by a trojan known as W32/DatCrypt, which encrypts files including office, image and MP3 files. When the user then tries to open any of these files, Windows reports them as being corrupted.
Data Doctor 2010 will allegedly repair files, for a price.
Rather than infected files, the latest scareware uses allegedly corrupted files to alarm users. The setup work is performed by a trojan known as W32/DatCrypt, which encrypts files including office, image and MP3 files. When the user then tries to open any of these files, Windows reports them as being corrupted.
Where previous encrypting trojans, such as GPCoder, have demanded a payment from the victim in order to decrypt files (ransomware), the criminals behind this particular attack have taken a more brazen tack. They offer the victim a program called Data Doctor 2010, which will allegedly repair the files, for download. The 'trial version' of Data Doctor downloaded then reports that it is only able to repair a single file, and that repairing all the user's files will require the full version costing around €90.
Happily for victims, anti-virus software vendor Sunbelt has provided a free downloadable tool (direct download) for repairing files without the intervention of Data Doctor. The tool simply decrypts the encrypted files, which use a simple encryption algorithm. Malware specialist FireEye reported a similar case back in early 2009. The alleged repair tool in that case was entitled FileFix Pro 2009 and was priced at €50.
Meanwhile Eset is warning of a new worm called Zimuse, which overwrites the master boot record on infected systems. BitDefender has also issued a warning about Zimuse, but claims that it destroys hard drives using malicious code. What is unanimously agreed is it does not do so immediately upon infecting a system but, depending on the variant, 20 or 40 days later by rendering the system unbootable. It is usually possible, however, to repair the system by using a repair CD to restore the MBR, allowing a normal Windows installation to once more boot.
Zimuse is being spread via infected USB sticks and via the web as a downloadable IQ test. Eset believes that the malware was originally targeted at members of a Slovakian bikers' club. Most initial reports on the spread of the worm came from Slovakia, but this has now been overtaken by the USA, followed by Slovenia, Thailand, Spain, Italy and the Czech Republic. Eset has provided a tool for removing the malware, but this is only useful before the MBR has been overwritten.
See also:
- From scareware to ransomware, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








