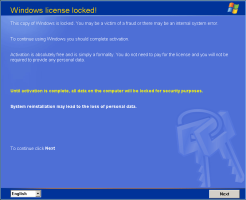
Ransomware claims to lock Windows licence
![]() Calls to unlock the computer are allegedly free.
Calls to unlock the computer are allegedly free.
Source: F-Secure
In what appears to be a lucrative scam, after infecting a system, ransomware blocks users from accessing their system and demands payment of a ransom to restore access. A recent variation on this theme claims to lock the Windows licence. The licence can be restored (re-activated) by calling a supposedly free service number.
However, the message is not generated by Microsoft – it's a trick and the call is, of course, anything but free. The numbers called are expensive international numbers in countries such as Madagascar. As anti-virus specialist F-Secure reports, calls are placed in a queue for several minutes to ensure that calling costs mount up. With the help of an operator, the fraudsters are able to divert the call to a cheaper country, allowing them to pocket a portion of the call charge to the number originally called.
Test calls made by F-Secure revealed that the code supplied to unlock the computer was always the same: 1351236. Whether this really unlocks a locked system is unknown – it's certainly worth a try. If this doesn't work, users are, as in similar scams, likely to be able to access their data and reinstall their systems using a boot CD.
This is a little trickier for users who have caught a dose of GPcode, which, as calls to the The H's associates at heise c't hotline prove, is once more on the rise. This is because this piece of malware encrypts the user's files. The encryption algorithm used is state of the art. GPcode creats a randomly generated 256-bit AES key on each infected system, which it uses to encrypt a number of files including all .doc, .rtf, Excel and PDF files.
It in turn encrypts the AES key using the fraudsters' public RSA key and saves only the encrypted version to the infected system. Consequently, the only way of restoring the system is to use the fraudsters' secret key. The encryption technique used is almost uncrackable and reverse engineering the malware is also fruitless. As Kaspersky's Nicolas Brulez notes in his analysis of GPcode, the only hope is a recent backup. Users who decide to play the blackmailers' game and pay up run the risk of losing their money and still not being able to access their data.
See also:
- New tool for GPcode trojan victims from Kaspersky, a report from The H.
- This Trojan encrypts data with RSA-4096 -- really?, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








