RE-Google aids code analysis
Together with a team of students from the University of Bonn, Felix Leder of the Honeynet Project has developed a code analysis tool which is able to render the functionality of machine code fragments comprehensible even to the relatively uninitiated. The 'RE-Google' plug-in for popular disassembler Interactive DisAssembler (IDA) Pro extracts constants, library names and strings from the indigestible disassembled binary code and uses it to search for code on Google.
Any source code files found by RE-Google are inserted into the assembler code listing. These frequently provide illuminating insights into the functionality of the program fragments in question – if, for example, they are networking code or encryption routines. Since RE-Google finds predominantly source code from higher languages, it frequently does away with the need for time-consuming and error-prone decompilation of the assembly language.
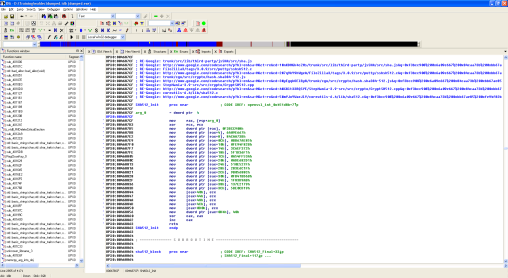
![]() RE-Google in action: Even without machine code knowledge, it's clear from the file names in the Google hits that the SHA-512 hash function is used in this code.
RE-Google in action: Even without machine code knowledge, it's clear from the file names in the Google hits that the SHA-512 hash function is used in this code.
"The tool was developed because we were frequently using search engines when analysing malware to try to work out what particular functions were doing," explained Felix Leder. The current versions delivers useful results for around 10 to 25 per cent of disassembled functions. This is often enough to work out the purpose of other linked functions. Leder notes "Each function which you are able to avoid having to explore in more depth represents a big time saving,".
RE-Google has already clocked up its first successes. According to Leder, they were able, with very little effort, to identify a number of cryptographic functions in the Conficker worm and the Waledac bot. In the case of Waledac, this represented a quarter of the code. Re-Google recognised the Zlib function in the Conficker code, despite the worm's author having gone to the trouble of removing any strings which might give the game away.
According to Leder, code obfuscation has no effect on the detection rate. Runtime packers do, however, necessitate a little preparatory work. "So far, the results tend to be a little too general," notes Leder, adding that his team is working on improved filtering techniques. The team is also working on adding further modules in order to automatically recognise a larger proportion of libraries by means of additional information.
Leder has previously been involved in various teams working on analysing the Conficker and Storm worms.
RE-Google is available to download (direct download) from the project's site and is released under version 3 of the GNU General Public License (GPLv3).
See also:
- RE-Google, the project's official project web site.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








