QuickTime opens up a security leak in Firefox
In a blog entry, the security specialist Petko Petkov (pdp) has drawn attention to a vulnerability via which attackers using specially crafted QuickTime media files can execute any JavaScript code in Firefox with maximum rights, or run programs on the computer. For this to work, Firefox has to be set up as the default browser and Apple's QuickTime (or QuickTime Alternative, according to some reports) has to be installed on the computer – hardly an unusual configuration.
The problem comes up when the QuickTime plug-in in Firefox processes QuickTime link files (.qtl). As a rule, these XML files contain a link to the actual media file and, in some cases, yet more control instructions that the QuickTime player obeys. QuickTime interprets these instructions even if the file has a different filename extension that is also associated with the QuickTime plug-in, such as .mov or .mp3.
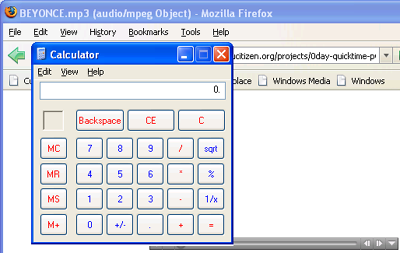
QuickTime link files can also execute any JavaScript via a modified filename extension.
Using the parameter qtnext in .qtl files, any JavaScript code can be executed in the browser. If an attacker also sets the -chrome switch there, the JavaScript runs in the chrome context – and thus has access rights to local resources. Petkov says an attacker can install any browser component this way – such as back doors, for example. If the user has administrator rights, any access at operating-system level would be conceivable. heise Security was able to reproduce the problem with Firefox 2.0.0.6 and QuickTime 7.2.0.240 under Windows XP with Service Pack 2.
But Petkov does not explain how users can protect themselves. Users report that the NoScript extension blocks the sample exploits that Petkov provides in his blog to demonstrate this security hole. When tested by heise security, the sample exploits did indeed fail if the NoScript extension was installed. Another alternative is to uninstall QuickTime. Affected uers should therefore either install the NoScript extension, set up a different default browser such as Opera, or uninstall QuickTime until Apple issues an updated software version.
- 0DAY: QuickTime pwns Firefox, security notice from pdp
(mba)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








