Protection from cross-site request forgery attacks beaten
A new technique shows how attackers can get round security measures intended to prevent Cross-Site Request Forgery (CSRF) attacks. CSRF, aka session riding, attacks involve websites changing things such as router configuration or blog content by using special embedded links. This generally requires the user both to be logged into the website on which the attack is to be made and to have the nefarious website open in the browser at the same time.
Tokens consisting of a single use random number, which are transferred between the server and client as part of the URL, are meant to protect against this kind of attack. Attackers cannot usually predict these tokens, with the result that their crafted links no longer work.
A security specialist that goes by the pseudonym Inferno has published details of how it's possible to obtain valid tokens, to allow successful CRSF attacks to be carried out, by using a brute force attack on the client. The method utilises a three-year old technique for reading the browser history via CSS.
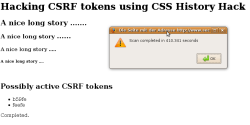
![]() Possible tokens found by the client script
Possible tokens found by the client script
Previously clicked links are displayed in the browser in a different colour to links to pages which have not yet been visited. The different colours are produced by a change in the style sheet for the HTML file, which the browser stores as an attribute in its history. By calling a long list of potential websites, it's possible to test the colour scheme for the style sheet and work out which websites have been visited.
Since, when carrying out a CSRF attack, the attacker knows the main URL, all he needs to do is test the possible token combinations – this is carried out client-side using JavaScript. Inferno has published a demo of his attack, which, in tests by the heise Security editorial team, The H's associated publication in Germany, was able to find two five-figure tokens in under seven minutes.
However, the tokens used to protect against CSRF attacks are usually much longer than this, meaning that, at present, finding tokens using this method would still be too time-consuming. Inferno recommends making tokens at least 8 characters in length and storing tokens in a hidden form field rather than the URL. Plug-ins such as SafeHistory for Firefox and the browser's special incognito mode also prevent websites from sniffing around the browser history.
See also:
- Attackers able to read out list of visited web pages, a report from The H.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








