"Printer Bomb" spread using compromised .htaccess files
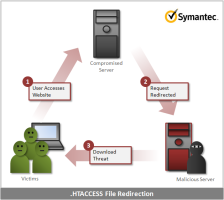
![]() Symantec's diagram of .htaccess redirection
Symantec's diagram of .htaccess redirection
Source: Symantec
Compromised .htaccess files on web servers allowed the "Printer Bomb" trojan to spread, says a Symantec researcher. The "Printer Bomb" trojan, named Trojan.Milicenso by Symantec, was notable for creating massive print jobs full of garbage characters that made printers run out of paper. The security company's initial investigations revealed malware exhibiting the common pattern of spreading either through malicious email attachments or through web sites hosting malicious scripts, and designed for delivering different payloads.
But further investigation has revealed that the malware uses modified .htaccess files on compromised web sites to silently send users to download the Milicenso malware. .htaccess files are used on web servers to help control access to directories and their contents on a per directory basis. They are also capable of rewriting URLs and redirecting browsers and it is this capability that the malware authors have been making use of. By uploading their own .htaccess file to servers, visitors to the compromised server can be silently sent to the malware author's site where trojans can be downloaded and installed.
According to Symantec, the redirection is carefully controlled by the .htaccess file. The rules come between 1600 blank lines at the top and bottom of the file to avoid being spotted by a casual reader. The rules say that users will only be redirected if it's their first visit to the site, that the link that led to the site was in search engine results or email (so bookmarked or pasted URLs won't work), and that the victim is running a popular web browser on Windows (so search engines don't pick up on the change).
Symantec believes the gang responsible has been using .htaccess redirection since at least 2010 and has, this year, been changing the domain the modified .htaccess sends users to on a daily basis. So far, 4000 different web sites have been identified redirecting users to the malicious sites, though most of them are personal or small business sites, a number of government, telecoms and financial services sites are also said to be compromised.
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








