Operation Ghost Click: FBI busts DNSChanger botnet
 Estonian prosecutors have co-operated with the FBI to arrest and bring charges against six individuals who have been accused of operating what is thought to be the largest known botnet to date. From 2007 until last month, the suspects allegedly infected more than 4 million computers in 100 countries with the DNSChanger malware. The prosecution has filed seven charges against the suspects, including Wire Fraud, which is punishable with up to 30 years imprisonment in the US.
Estonian prosecutors have co-operated with the FBI to arrest and bring charges against six individuals who have been accused of operating what is thought to be the largest known botnet to date. From 2007 until last month, the suspects allegedly infected more than 4 million computers in 100 countries with the DNSChanger malware. The prosecution has filed seven charges against the suspects, including Wire Fraud, which is punishable with up to 30 years imprisonment in the US.
The FBI estimates that 500,000 systems were infected in the United States alone; computers in Germany were apparently also infected, but the US agency hasn't provided any figures. The FBI said that victims included private individuals as well as businesses and government entities such as NASA. The investigations took place over a period of two years. The US authorities are currently seeking the extradition of the suspects to the US.
The gang is said to have operated several companies that offered internet advertising and traffic, or guaranteed web page views. According to the FBI, the ads were displayed on infected computers when users visited popular web sites – instead of the web site operators' own ads. The FBI added that the traffic was created by redirecting domains to other web pages, and that the thieves were able to generate at least $14 million in illicit fees.
![]()
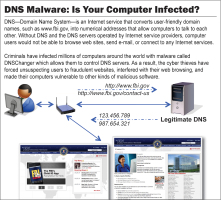
Source: fbi.gov
They achieved this by manipulating the network settings on their victims' computers via the DNSChanger malware. The malware redirects a legitimate DNS server's IP address to rogue servers controlled by the attackers. When a victim's computer initiates a DNS query, for example, for the apple.com domain, a bogus IP address will be returned, and instead of Apple's home page, the victim is instead directed to a page that is controlled by the attackers.
To get other clients on a local network to accept the rogue DNS server, the malware also acts as a DHCP server. Consequently, the DNS manipulations also affect computers or smartphones that haven't been infected. DNSChanger also tries to modify the DNS server that is listed in the user's router. If the router's web interface is password protected, the malware will try out various default passwords. The FBI said that, to avoid being detected, DNSChanger prevents anti-virus software from updating its virus signatures.
The attackers' DNS servers can be found in the following address ranges: 85.255.112.0 to 85.255.127.255, 67.210.0.0 to 67.210.15.255, 93.188.160.0 to 93.188.167.255, 77.67.83.0 to 77.67.83.255, 213.109.64.0 to 213.109.79.255 and 64.28.176.0 to 64.28.191.255. If an IP address from these ranges is listed as the DNS server on a computer or router, the device is likely to be infected with DNSChanger. The FBI has released instructions![]() on how to find this information under Windows or Mac OS X.
on how to find this information under Windows or Mac OS X.
As an immediate measure, the FBI has taken down the malicious DNS servers. To provide uninterrupted internet access for infected systems, the investigators have replaced the rogue servers with legitimate DNS servers that are accessed via the listed IP addresses. However, the substitute servers will only operate for a period of four months – users who haven't detected their infections after this grace period will no longer be able to access the internet.
(crve)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








