Open source tool enables security tests for chip cards

At this year's Black Hat Conference, crypto expert Karsten Nohl of SRLabs demonstrated the degate tool that can be used to take a closer look at applications stored on smartcards, such as credit cards and SIM cards.
A smartcard chip is a tiny computer with ROM, in which its operating system and application are located; it also has flash memory for dynamic data, an execution unit and RAM. The ROM, RAM and flash memory are connect to the execution unit via buses. The chips often contain important data such as keys for pay-TV programmes and programs for generating TANs, which is why there have been regular and repeated attempts to read them out. "Timing attacks" were a popular approach up until a few years ago, but this has been succeeded by intrusive attacks on the chip's buses.
Ten years ago, industry reacted to the upcoming hacking risk by implementing data encryption on smartcards. This protection is necessary because ROM contents can be read with a simple optical microscope. For data encryption, very fast crypto algorithms have to be used to protect the Flash/RAM/ROM, typically while the data is on the bus within one the CPU's clock cycles. Development to protect software has hardly progressed beyond this encryption. Furthermore, some of the ROM has to stay unencrypted though because the encryption unit first has be loaded with the decryption key so that the card's software can work with its encrypted memory.
Researchers on Karsten Nohl's team have now used an open source tool to reconstruct, from the silicon implementation, the hardware algorithms used internally . To do so, microscopic photographs were taken of the chip's silicon, and then each individual logic element, the "gates", are marked with the tool. When all connections between these silicon gates have been marked with the software, degate produces logic code that allows for emulation of the chip and understanding of its algorithms.
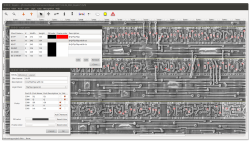
![]() A microscopic image reveals the structure of the smartcard chip. The degate tool allows its encryption to be reverse engineered.
A microscopic image reveals the structure of the smartcard chip. The degate tool allows its encryption to be reverse engineered.
Source: SRLabs
Once the encryption algorithm for ROM is known, the researchers needed to find the key for it. Often, the key is stored in the inexpensive, and optically readable, ROM to save money instead of in flash memory. If programs and the operating system are stored on the smartcard's ROM, they can be read out and decrypted given a knowledge of the secret encryption algorithm. Then, insecure implementations and security-related software errors can be detected and exploited.
In contrast, keys and dynamic data are much better protected when stored in flash memory (or EEPROM). This is because the tools needed to read such memory are extremely expensive, costing millions of pounds. The same holds true for RAM content.
Even the most secure hardware chip can be attacked if insecure programs are on it. Now that degate, is available for finding such bugs, criminals can be expected to join the "good guys" in testing security levels. For instance, they could crack weak TAN generators or clone electronic ID cards. New attacks on pay-TV systems that use only a few keys for a large number of users are also likely. The next security focus for smartcards will therefore have to be the quality of the software running on hardened chips.
(ehe)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








