New critical vulnerability in Internet Explorer
Last Friday, a posting entitled "IE7" and containing only a few uncommented lines of HTML code appeared on the BugTraq security mailing list. Several security firms have since confirmed that the code demonstrates a previously unknown security hole in Internet Explorer.
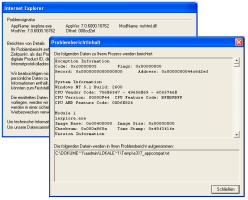
![]() heise Security found Internet Explorer currently crashes when trying to access the exploit code
In first tests by heise Security, Internet Explorer crashed when trying to access the HTML page. Security firm Symantec confirms that, while the current zero day exploit is unreliable, more stable exploit code which will present a real threat is expected to appear in the near future. French security firm VUPEN managed to reproduce the security problem in Internet Explorer 6 and 7 on Windows XP SP3, warning that this allows attackers to inject arbitrary code and infect a system with malicious code. Microsoft has not yet commented on the problem.
heise Security found Internet Explorer currently crashes when trying to access the exploit code
In first tests by heise Security, Internet Explorer crashed when trying to access the HTML page. Security firm Symantec confirms that, while the current zero day exploit is unreliable, more stable exploit code which will present a real threat is expected to appear in the near future. French security firm VUPEN managed to reproduce the security problem in Internet Explorer 6 and 7 on Windows XP SP3, warning that this allows attackers to inject arbitrary code and infect a system with malicious code. Microsoft has not yet commented on the problem.
The real identity of sender "securitylab.ir" remains unknown, but the pseudonym has appeared in advisories and exploits across various areas since April 2009. The flaw appears to be triggered when calling the getElementsByTagName JavaScript method. This means that IE users can protect their systems by disabling the Active Scripting settings for the internet zone, although as a result, many web pages will no longer function. As the flaw can be traced to Microsoft's mshtml.dll library, it is unlikely that other browsers are affected
(djwm)








![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/6/7/2/comingin310_4_kicker-4977194bfb0de0d7.png)

![Kernel Log: Coming in 3.10 (Part 3) [--] Infrastructure](/imgs/43/1/0/4/2/3/2/3/comingin310_3_kicker-151cd7b9e9660f05.png)








